vSOC SPOT Report: Google Chrome FileReader Vulnerability
Posted by: GuidePoint Security
Overview
On March 1, 2019, Google quietly patched Chrome, then announced days later the update had fixed CVE-2019-5786, a vulnerability discovered by Google researcher Clement Lecigne in February. Google made the announcement due to the existence of exploits in the wild. Google rates the issue as high severity.
Neither MITRE nor NIST have writeups for this CVE in their databases at the time of this writing. Searching on CVE-2019-5786 at either site retrieves a placeholder page.
Technical Overview
The vulnerability exists in Chrome’s FileReader API and exploits a memory flaw called a Use-After-Free condition that either allows an attacker to run arbitrary code outside of Chrome’s security sandbox or crash the browser. The FileReader API is intended to allow the browser to read and access locally stored files.
An attacker can use this flaw by placing the exploit on a specially crafted web page and getting would-be victims to view it.
Google has not released details of the vulnerability beyond the type of flaw and the ability to use it to run executable code.
Potential Impact
Since the attacker can run arbitrary code on your machine, the potential impact is nearly limitless, including but not limited to loss or destruction of data, system outages, and malicious code running on your systems.
While the most likely target of this flaw is Windows systems, the flaw exists in all versions of Chrome for all operating systems. If you run Chrome on other operating systems, such as Mac OS X or Linux, be sure to update those as well, not just your workstations running Windows.
What You Should Do
Update Chrome to version 72.0.3626.121 as soon as possible. To verify the version you are running on the client-side, enter the URL chrome://settings/help
Tenable customers can scan their networks using plugin ID 700422. At the time of this writing, Qualys did not yet have a signature for CVE-2019-5786 but Qualys customers can navigate to VM > Assets > Application and search for Chrome to see what versions are running in their environment. The list is exportable in CSV format.
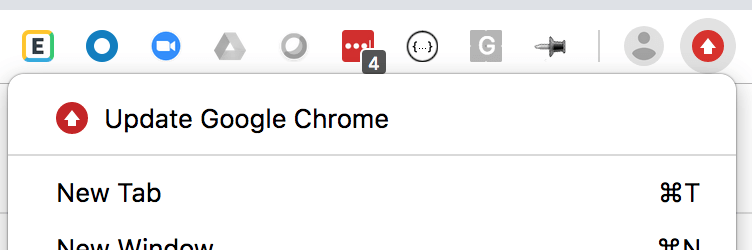
Chrome provides user feedback indicating when it needs an update by placing an arrow in the upper right corner of its screen next to the menu icon, but in limited testing vSOC found the arrow doesn’t necessarily show 100% of the time. An example screenshot appears below.
GuidePoint’s vSOC will provide additional information as it is made public to help protect our clients.
Supporting Information
- https://nakedsecurity.sophos.com/2019/03/06/serious-chrome-zero-day-google-says-update-right-this-minute/
- https://www.zdnet.com/article/google-reveals-chrome-zero-day-under-active-attacks/
- https://www.bleepingcomputer.com/news/security/google-chrome-update-patches-zero-day-actively-exploited-in-the-wild/
- https://thehackernews.com/2019/03/update-google-chrome-hack.html
Contributing Authors
Dave Farquhar, vSOC Identify Program Manager