Embracing Zero Trust with Google BeyondCorp
Posted by: Jonathan Villa
Although the cloud facilitates and simplifies Zero Trust architectures’ implementation, there is still work to do for it to be useful. While several cloud providers have implemented Zero Trust solutions, I’ll focus on Google’s BeyondCorp access management solution.
The standard corporate approach to secure data access anywhere is still the Virtual Private Network (VPN). This solution often requires an agent to be installed upon the endpoint that introduces high amounts of latency to the connection and is challenging to scale and secure. Now I’ll examine a Zero Trust alternative to this often problematic VPN implementation, BeyondCorp.
Google developed BeyondCorp in 2011 as a response to incidents of nation-state supported attacks against top tier Silicon Valley companies in years prior. At that time, Google’s stated goal was “to enable Google employees and our extended workforce to work successfully from untrusted networks on a variety of devices without using a client-side VPN.”
BeyondCorp takes this intent and extends it far beyond the necessary capabilities of a VPN. Google’s solution has been tested, at scale, by its employees for the last 9+ years. During that period, Google has shown that these solutions are scalable, maintainable, and, most importantly, secure.
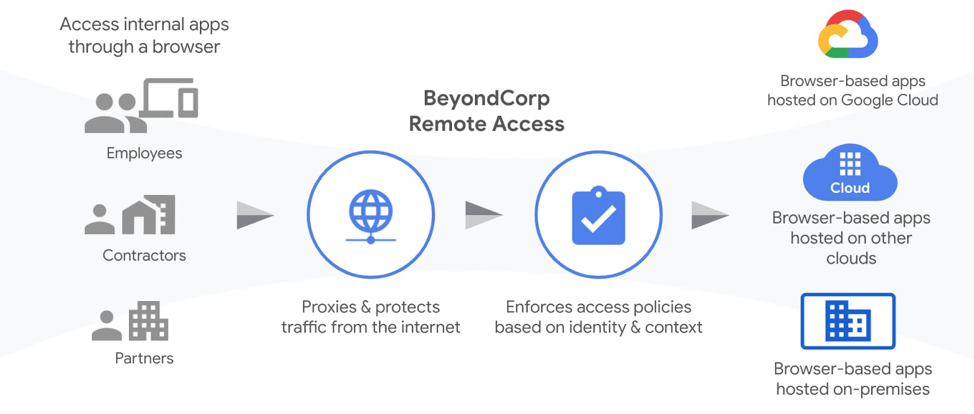
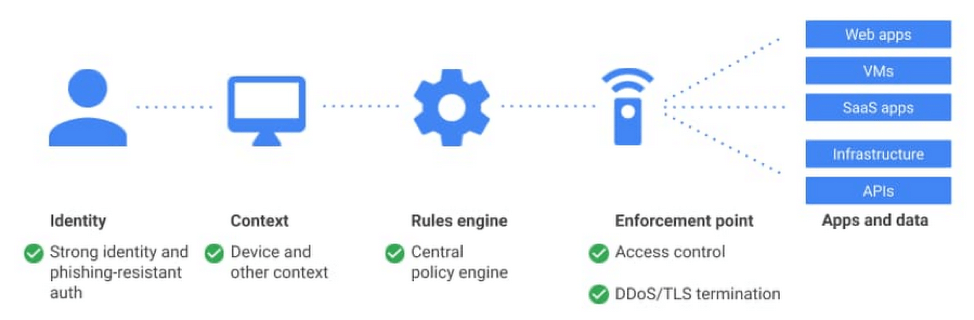
Deploying a Zero Trust Application
Let’s walk through a proof of concept application enablement of the internal Acme “Unicorn App.” This application was developed in-house, run in the cloud and is key to the sales organization that had previously worked out of regional offices. Disruption has occurred resulting in the entirety of the sales organization operating remotely. IT is tasked with quickly provisioning access to this app so that the sales team is not disrupted.
The first step is to identify the users. For this, Acme will leverage Google Identity, though any SSO provider with support for Multi-Factor Authentication would be a wise choice. For an extra layer of authentication, Acme also chooses to deploy Google Endpoint Verification. This supports both the company-owned assets deployed via the G-Suite control panel and provides employees the opportunity to add it to their devices. Together these systems provide the data to power the context-based access controls Acme will configure in the next step.
Step two is to configure the rules that will allow or reject incoming connections based upon the user and device context. Acme is all in on Google and selects the Access Context Manager rules engine. This enables the IT Admins to create policies to allow or disallow access when a specific user and device context is matched. Admins can craft one set of rules and apply them across a variety of applications or organizations. Acme has decided that with the sensitive nature of sales data, only company-owned devices, with current patches and disk encryption enabled, connecting from the Americas and EMEA will be authorized. To protect against phishing attacks, they have provided the sales team with FIDO keys and enabled MFA as a required connection component.
Step three is the Identity Aware Proxy that sits in front of every connection request. This applies the context-aware ruleset, enforces encryption, and provides DDoS protection and TLS termination. IAP’s are near-zero latency solutions that don’t impact the user experience while significantly enhancing the security of the organization’s services.
The final step is the connection to the Unicorn App. No changes were required for the app. It is not exposed externally and it is the same application that was deployed previously and exposed to the internal network.
All of the above systems and services can be quickly provisioned with minimal IT overhead and limited employee endpoint configurations. These features allow an organization to roll out Zero Trust networks to promptly secure, context-aware access to various internal and external applications.
While Google pioneered the concept of Zero Trust with BeyondCorp, industry adoption was quick, and there is a multitude of vendors offering services to enable your organization to move to a Zero Trust model. You can read more on BeyondCorp and Zero Trust in our Securing Your Remote Workforce In The Cloud Ebook.
Jonathan Villa
Practice Director - Cloud Security ,
GuidePoint Security
Jonathan Villa has worked as a technology consultant since 2000 and has worked in the information security field since 2003. For more than 10 years, Jonathan worked with a large municipality as a senior consultant in several competencies including PCI compliance and training, web application architecture and security, vulnerability assessments and developer training, and web application firewall administration. Jonathan also co-architected and managed an automated continuous integration environment that included static and dynamic code analysis for over 150 applications deployed to several distinct environments and platforms.
Jonathan has worked with virtualization and cloud technologies since 2005, and since 2010 has focused primarily on cloud security. Jonathan has worked with clients in various verticals across North America, South America and Asia to design and implement secured public and hybrid cloud environments, integrate security into continuous integration and delivery methodologies and develop custom application and security solutions using the AWS SDK. He has also provided guidance to customers in understanding how to manage their environments under the Shared Responsibility Model.
In addition to providing PCI training, Jonathan also has presented to law enforcement on cybersecurity and was a speaker at the Cloud Security Alliance New York City Summit. Jonathan holds the following certifications: CISSP, CCSP, C|EH, PCIP, AWS Certified Solutions Architect – Professional, AWS Certified SysOps Administrator, AWS Certified Developer, AWS Certified DevOps Professional and Security+ certifications including the CSA Certificate of Cloud Security Knowledge.