
GRIT Ransomware Report: April 2023
Additional contributors to this GRIT report: Grayson North, Nic Finn, and Drew Schmitt
Following a relatively active March–resulting in 451 affected organizations observed across 24 ransomware leak sites–GRIT observed interesting movement in the ransomware landscape in April. Most notably, Clop, a Full-time group we described in detail in 2023’s first quarterly report, dropped from 128 reported victims in March to just three in April, reflecting our assessment that Clop’s March spike resulted from their aggressive use of an exploited vulnerability.
Outside of Clop, the smaller ransomware Splinter and Ephemeral groups Stormous, Play, and Ransomhouse experienced the largest decrease in reported victims in April, each seeing a drop of 50% or more in victim count.
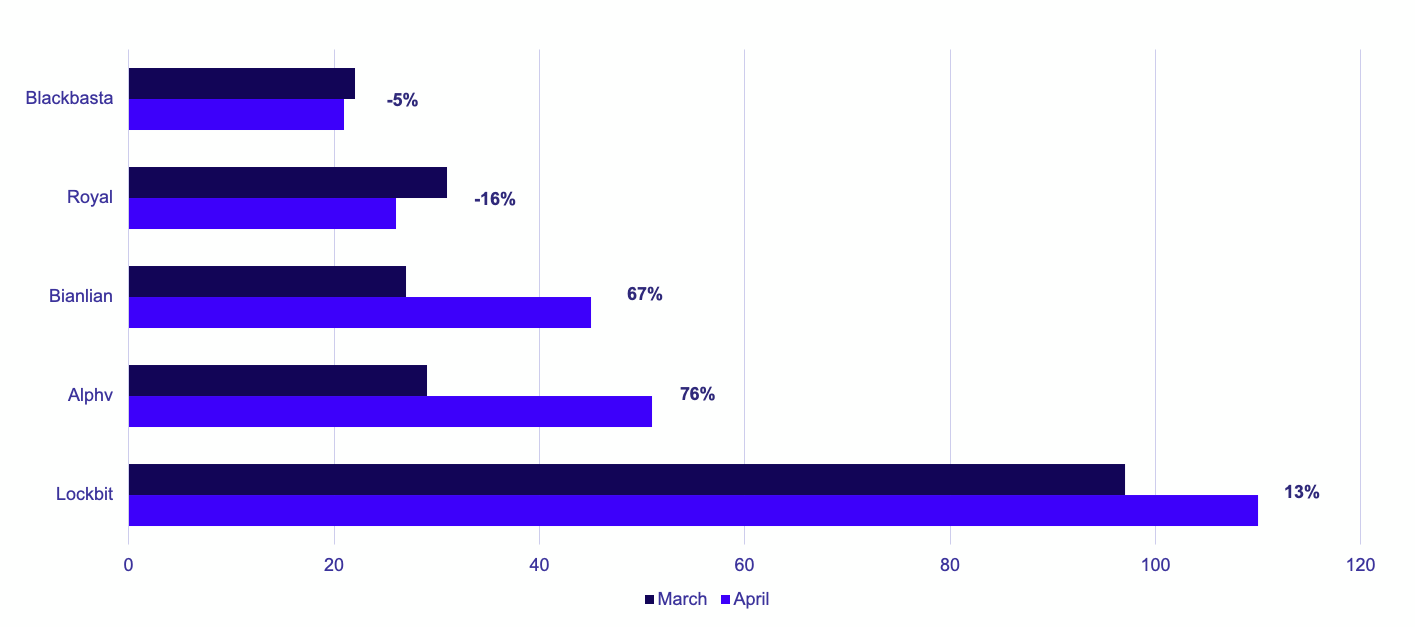
Alphv, a Full-time ransomware group also known as BlackCat, showed the largest monthly increase, going from the fourth-most active group in March to the second-most active group in April. Bianlian was close behind, shifting from the fifth to third-most active group. Lockbit, still the most impactful Full-time ransomware group by far, demonstrated the third-largest increase in victim volume, reflected in a victim count that was twice that of any other ransomware group in April.
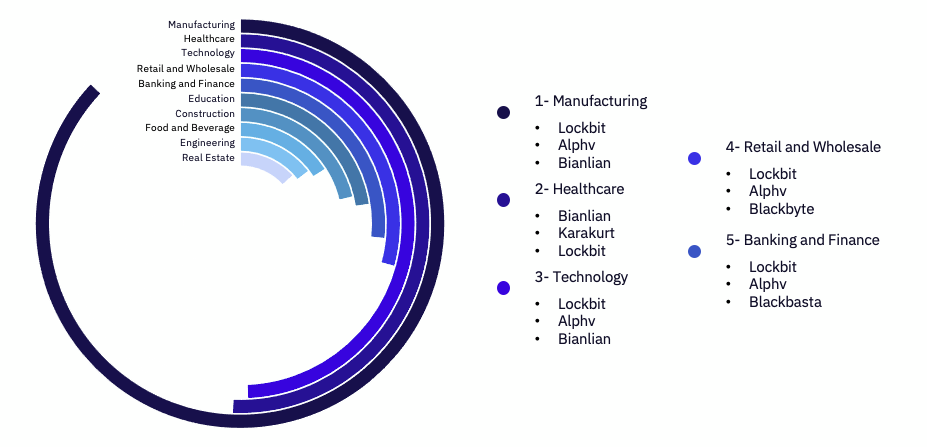
We again observed Manufacturing as the most-affected industry, accounting for 19% of all reported victims and experiencing a 46% increase in victim volume from 46 to 67 between March and April. This increase is notable as it occurred amongst a substantial decrease in overall ransomware victim volume between March and April. We also observed an increase in victims from the healthcare industry in April, with the Full-time group Bianlian alone impacting 11 victims, followed by Lockbit and Karakurt accounting for seven victims each. Of note, victims in the healthcare industry represented 64% of Karakurt’s victims, doubling their healthcare victims from the preceding months.
From a geographical perspective, we observed similar ransomware impacts from March to April. The United States remains the most-impacted country by far, with its healthcare industry as the most frequently impacted. Among Full-time ransomware groups, Royal and Alphv appear to strongly prefer US organizations, which account for 77% and 51% of their victims respectively. GRIT observed a more diversified impact by the ransomware group Play, which was most heavily associated with Western European targets, and only 14% of victims from the United States.
Ransomware Trends
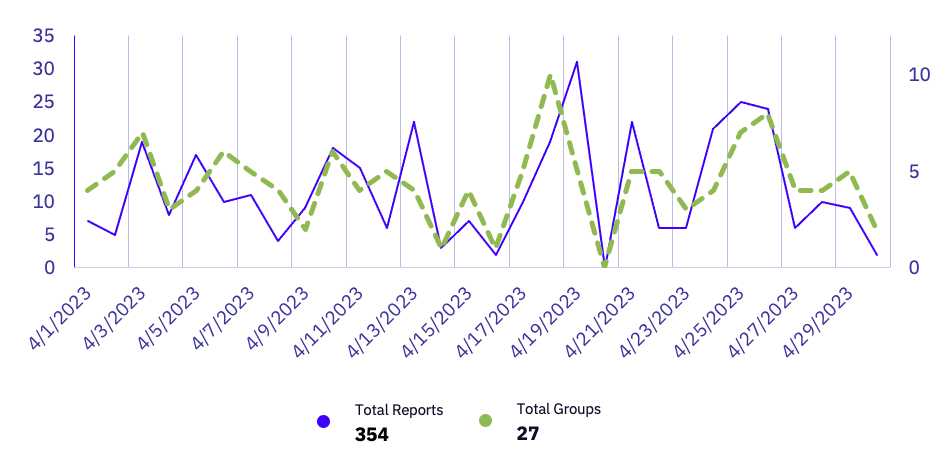
GRIT observed a 22% decrease in total affected organizations from March 2023 to April 2023. In spite of this, April’s affected organizations increased year-over-year, up 27% from 279 observed victims in April 2022.
April 19th was the busiest day in terms of reported victims, with Bianlian posting 40% of their monthly total on this day alone – including five affected healthcare victims.
We observed a diverse slate of active threat groups in April 2023, with 27 unique groups. This level of diversity, the highest that GRIT has observed since November 2021, reflects the continued threat and viability of smaller ransomware groups, including newly established Splinter or Ephemeral groups consisting of experienced ransomware operators.
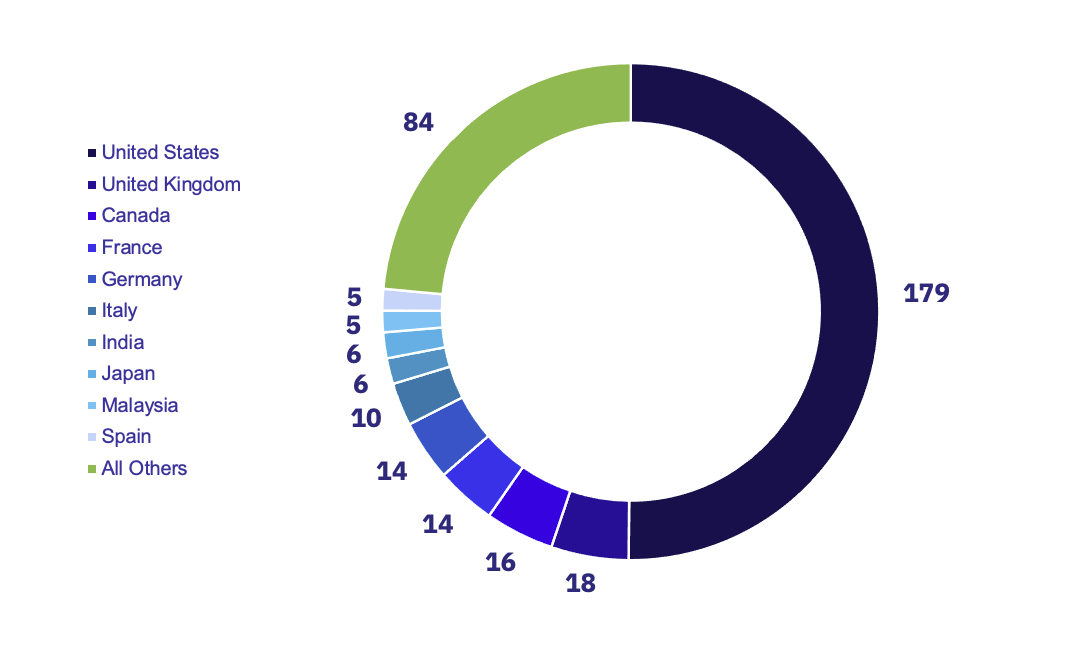
Ransomware Victims by Country
This month’s top 10 victim countries are similar to many in the past, with the United States amassing 179 victims and the United Kingdom and Canada coming in distant second and third place with 18 and 16 victims respectively. Germany and France both had 14 reported victims, Italy saw ten reports, and all other countries had less than ten victims.
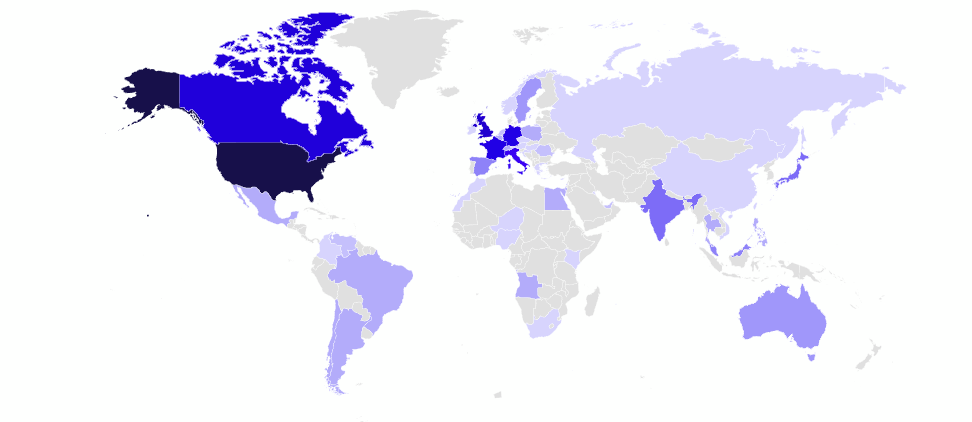
From March to April 2023, GRIT observed a slight drop in the number of impacted countries, from 55 down to 53. The groups most actively targeting the United States were Lockbit, Bianlian, and Alphv.
Lockbit again demonstrated dominance in the ransomware landscape with victims reported from 39 countries and 28 industries. Despite a decrease in total reported victims for the month, the share of impacted organizations from the United States increased from 48% to 51%.
Ransomware Victims by Industry
Lockbit, Bianlian, and Alphv weren’t just the most active threat groups targeting the United States, they also dominated the most frequently impacted industries. It follows, then, that industries in the United States, the United Kingdom, and Germany were all targeted the most frequently.
Within the most heavily attacked countries, ransomware groups impacted 27 industries in the United States, 11 in the United Kingdom, 11 in both Canada and France, and 7 in Germany.
Across all observed victims, 23 impacted industries saw a decrease in total claimed attacks compared to March 2023. Most notably, attacks against Government targets dropped by 15 (a 79% decrease), Automotive by 12 (an 86% decrease), Transportation was down by 11 (a 55% decrease), Telecommunications dropped by 9 (a 75% decrease), and Legal also fell by 9 (a 47% decrease).
Cumulative Victims by Threat Group
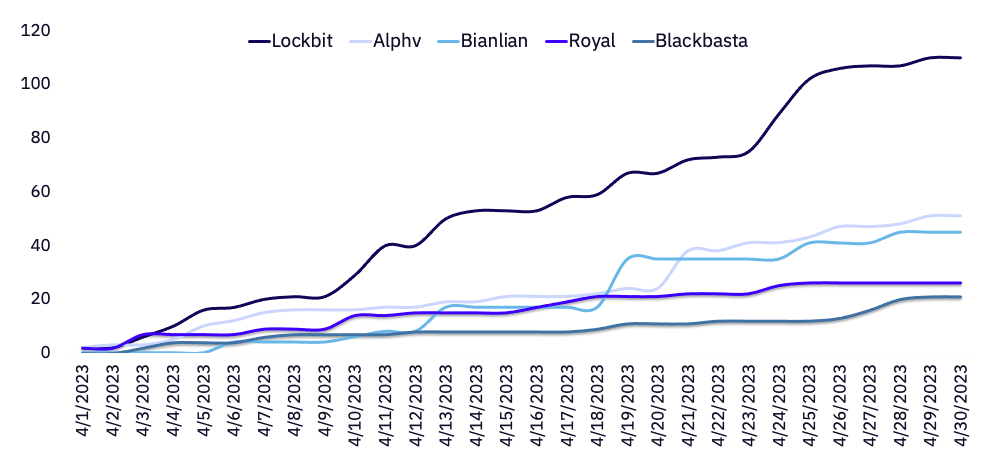
Averaging almost four victims per day (3.7), Lockbit increased their total number of affected organizations from 97 to 110 over the past month, impacting organizations across 39 countries.
Alphv nearly doubled their number of impacted organizations compared to March, increasing their share of total observed victims from 6% to 14% in April 2023. Alphv also focused heavily on publicizing their attack and extortion of Western Digital.
April 2023 represents Bianlian’s most impactful month since GRIT began tracking their activity. Bianlian’s victim count continues to increase month-over-month, from 15 in February, to 27 in March, to their current high of 45 in April.
Threat Actor Spotlight: Alphv / BlackCat

Alphv (stylized as ALPHV), also known as BlackCat or Noberus, was the second most active ransomware group in April 2023, responsible for 14% of total observed victims.
First observed in November 2021, Alphv is believed to consist of experienced ransomware operators from REvil, Darkside, BlackMatter, and other groups. They are the first prominent ransomware group to program their encryptor in the Rust programming language, which is considered to be more secure and harder to reverse engineer than more common languages including C and C++.
GRIT has observed 271 victims claimed by Alphv over the past year, with most of their victims belonging to the Manufacturing (10%), Legal (9%), Banking & Finance (8%), Technology (8%), and Construction (6%) industries. They disproportionately impact victims in the United States, which represents 51% of their claimed victims. Australia, Canada, Germany, India, and the United Kingdom are also among the leading impacted nations, each representing 3-5% of observed victims.
Open-source security reporting suggests that Alphv takes a “big game hunting” approach to ransomware, actively seeking targets with high revenues and seeking correspondingly high ransoms; publicly reported initial ransom demands for larger victims can range from $2.5 million to over $10 million USD.
Alphv performs “double-extortion” attacks, where the actor exfiltrates and threatens to leak sensitive data as additional leverage to obtain ransom payment from victims. Alphv also practices what is commonly referred to as “triple-extortion”, in which they threaten to conduct Distributed Denial of Service (DDoS) attacks, or otherwise selectively publish information to cause reputational harm against non-compliant victims. For more information and analysis of increasingly coercive extortion methods ransomware groups deploy, see the Q1 2023 GRIT Ransomware Report.
Alphv’s most common initial access vectors include exploiting Microsoft Exchange Server vulnerabilities and the use of compromised credentials to gain remote access. Security researchers have also observed Alphv’s use of the Emotet botnet in deploying Alphv ransomware, as well as the use of the offensive security tool, Cobalt Strike.
Other Notable Ransomware Events
Nokoyawa Ransomware Attacks with Windows Zero-Day
In early April, security researchers at Kaspersky observed ransomware threat group Nokoyawa’s exploitation of vulnerability CVE-2023-28252 prior to the availability of a patch. CVE-2023-28252, a privilege escalation vulnerability in the Common Log File System (CLFS) of Windows, was patched as part of Microsoft’s Patch Tuesday on April 11, 2023. The vulnerability enables an attacker to elevate to SYSTEM privileges using a binary dropped on the system. Kaspersky observed Nokoyawa using the zero-day to escalate privileges on a compromised system and to dump credentials. The threat actor was then able to use these credentials to move laterally to sensitive systems and ultimately deploy ransomware on the victim’s environment. GRIT recommends installing the patch for this vulnerability as soon as possible and monitoring for further exploitation of the CLFS, as its attack surface has been recently explored by security researchers and threat actors alike.
Alphv’s Escalation of Coercive Tactics (Western Digital)
In GRIT’s first Quarterly Ransomware Report of 2023, we noted several instances of threat actors escalating their post-exploitation coercion tactics in hopes of compelling more victims to pay their ransom. This month, Alphv provided another example of the trend as they released public statements targeting Western Digital, a victim they allegedly ransomed in late March. After the reported “8 figure” ransom went unpaid, Alphv posted a series of messages on their data leak site expressing their distaste for Western Digital and their leadership. Alphv later released screenshots of emails, Teams chats, and even a Zoom meeting, proving that they still had access to the environment as the victim struggled to respond to the incident.
Avoslocker Escalation of Coercive Tactics (Bluefield University)
In April, Bluefield University–a private university in Virginia–allegedly became a victim of Avoslocker ransomware. After the ransom demand presumably went unpaid, the threat actor escalated communications by leveraging the school’s “Ramalert” emergency alert system. The system, designed to communicate with students via text message in emergency situations, appeared to be compromised at some point during the incident, allowing Avoslocker access to send messages to all students. The series of text messages sent by the threat actor included a link to their data leak site, with the promise that the school’s and students’ data would begin appearing as early as May 1st if payment was not made. We note that this is the first known occurrence of a mass SMS messaging system being used this way by a threat actor. This incident reflects the growing trend of threat actors alerting customers and clients of organizations in an attempt to increase coercive leverage and generate reputational harm.
New Ransomware Groups Tracked by GRIT in April 2023
Akira
Akira appears to be an independent ransomware operation that has demonstrated an affinity for aggressive tactics–including rendering systems unusable–depending on the malware being used during their operations. Although Akira is suspected of having operated for quite some time, as of April 2023, they have begun publishing victims to their “name and shame” leak site. Akira publicly claimed nine victims in April, mostly impacting the Education and Manufacturing industry in the United States.
CryptNet
CryptNet was first spotted in mid-April attempting to recruit ”skilled pen testers” with experience in Active Directory and Network operations. CryptNet operates as a Ransomware as a Service (RaaS) group that claims to have the “fastest ransomware in the world,” a claim previously limited to Lockbit and a group branded “Rorschach” by security researchers. Additionally, CryptNet insists that they maintain no limits on eligible countries to target (including Russia and China) and that affiliates get to keep 90% of any ransom payment successfully negotiated. During April, GRIT observed two public victims claimed by CryptNet, both within the United States.
CrossLock
CrossLock is a Go Programming Language-based ransomware that began publicly posting victims to their leak site in April. A notable characteristic associated with CrossLock is their ability to perform Event Trace bypass techniques that can assist with defense evasion during execution. CrossLock’s decision to use Go as their language of choice ensures that they have cross-platform capabilities for impacting both Windows and Linux environments. We observed CrossLock’s posting of a single Brazilian organization from the technology industry to their leak site in April.
Trigona
GRIT began tracking victims associated with Trigona in April, although intelligence reporting suggests operations began as early as October 2022. Security researchers have noticed that Trigona has similarities to the CryLock ransomware, suggesting that the operators of CryLock may have rebranded as Trigona ransomware. Trigona has also been observed attempting to use Alphv’s likeness to give themselves credibility during the extortion process. We observed five victims attributed to Trigona in April.
Dunghill_Leak
GRIT began tracking Dunghill_Leak as a suspected rebrand of the DarkAngels ransomware group in April. In April, the Dunghill_Leak site claimed a single victim in the Technology sector. While limited details regarding Dunhill_Leak are available as of the publishing of this report, available analysis of ransomware executables associated with Dunghill_Leak indicates a strong likeness with DarkAngels and Babuk ransomware families.
Final Thoughts
The intensity of ransomware operations in April decreased from the preceding month, with corresponding reductions in “spikes” of activity on individual days. GRIT continues to observe the majority of published ransomware victims as attributed to Full-time ransomware groups–including Lockbit, Alphv, Bianlian, Royal, and BlackBasta. These organizations are often assessed in open-source security reporting as consisting of experienced operators from legacy ransomware organizations, accounting for their advanced tactics, increased victim counts, and application of novel techniques, including “triple extortion” methods.
We observed a more diverse slate of smaller ransomware groups operating in April, often claiming only a handful of victims and an unknown number of victims who may have paid the ransom. This is probably supported by operators from Splinter and Ephemeral ransomware groups with experience in other ransomware organizations, as well as the decreased barriers to entry afforded by the modern Ransomware-as-a-Service (RaaS) ecosystem. We have previously assessed that these smaller Splinter and Ephemeral groups may take advantage of their low profile to successfully target victims with access to sensitive information, dodging sanctions and demonstrating TTPs less well-known than their Full-time counterparts.
We note the continued presence of novel coercive techniques amongst the larger ransomware groups and assess that the increased use of these techniques by smaller groups may be indicative of their perceived efficacy in the ransomware community. While it is impossible to tell at this point to what extent these techniques may be effective in increasing compliance, we expect to see continued adoption across more groups due to the ease of execution and to introduce greater uncertainty into the ransomware settlement process.
The GRIT Ransomware Taxonomy
By subdividing ransomware groups, GRIT can obtain more detailed insights into how ransomware groups progress in their level of operational maturity and can classify and identify potential rebranding activity.
We distinguish ransomware groups by placing them into these four categories:
FULL-TIME
These groups have been active for nine or more months and often have months where they publicly claim 10 or more victims. Their standardized infrastructure and defined affiliate structure (if acting as Ransomware as a Service) lead to consistent TTPs and behaviors with only slight variations based on the ransomware operator.
REBRAND
These groups have typically been active for less than nine months, but their public posting rates regularly rival Full-time groups. TTPs for this type of group are more varied than a Full-time group, yet still project an organized and determined operational capability. If the rebrand wasn’t announced publicly, these groups’ TTPs will help identify their previous identity.
SPLINTER
These groups are established and have been active for 2-5 months with varied public posting rates. Their TTPs are varied, sometimes borrowed, and indicative of less experienced operators that are developing their brand and identity. If their split from another group wasn’t public information, their TTP overlap with known groups can give them away.
EPHEMERAL
These groups have been active for less than two months, with varied, but low, victim rates. These groups are often a “flash in the pan” and do not progress to more developed and mature group types.
There are multiple routes a group can take through the various classifications, and no one route is standard. While one group may begin as “Ephemeral” and move their way through the ranks to “Full-time,” another group may enter as a “Rebrand” as part of a larger obfuscation strategy to avoid attention from law enforcement.