
GRIT Ransomware Report: August 2022
Ransomware Trends
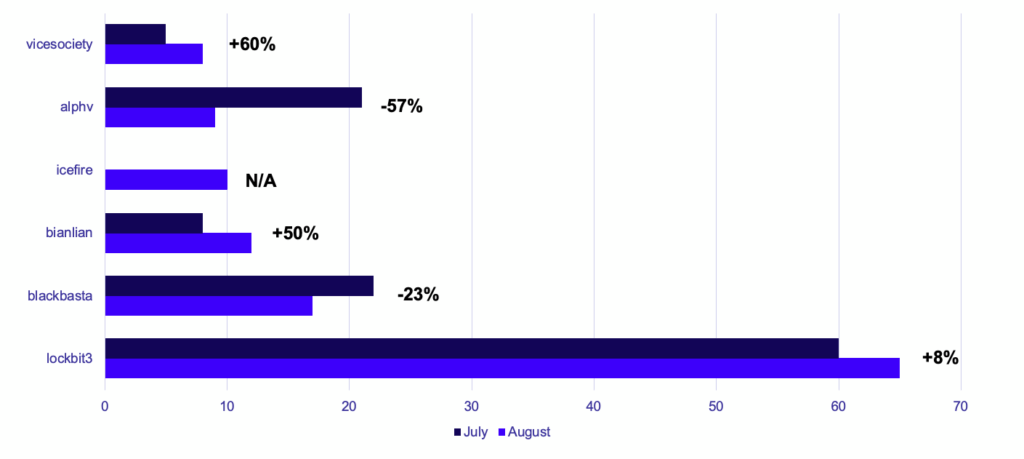
In August, GRIT saw a slight downward trend in total ransomware reports (from 187 to 176, a 5.88% drop), with eight groups showing a decline in reports compared to July. Specifically, six groups had a 50% or more decline in public postings including Yanlouwang, Hive, Lorenz, AlphV, Onyx, and Cuba. The Hive ransomware group was especially notable due to their drop from 26 victims in July to only 7 victims in August.
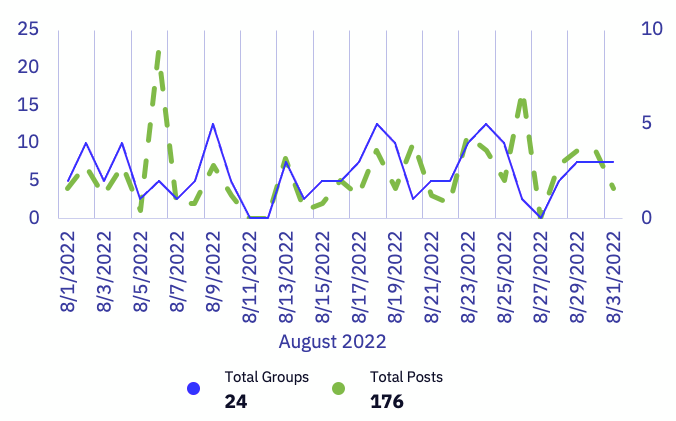
Despite the small decrease in the total number of publicly posted victims, August brought a 19% increase in active groups. Donut Leaks and IceFire publicized victims for the first time, and we also saw some leaks by groups that had no activity in July, including Snatch, Daixin, and RansomEXX. Conversely, 0mega and Red Alert were the only groups active in July that did not claim any victims in August.
Technology and Manufacturing were the most impacted industry verticals, each moving up one spot and overtaking Retail and Wholesale. In fact, the Food and Beverage, Real Estate, Retail and Wholesale, and Media and Advertising industries saw the biggest decrease in targeting compared to July, while Pharmaceutical, Education, and Healthcare saw a sharp increase compared to July.
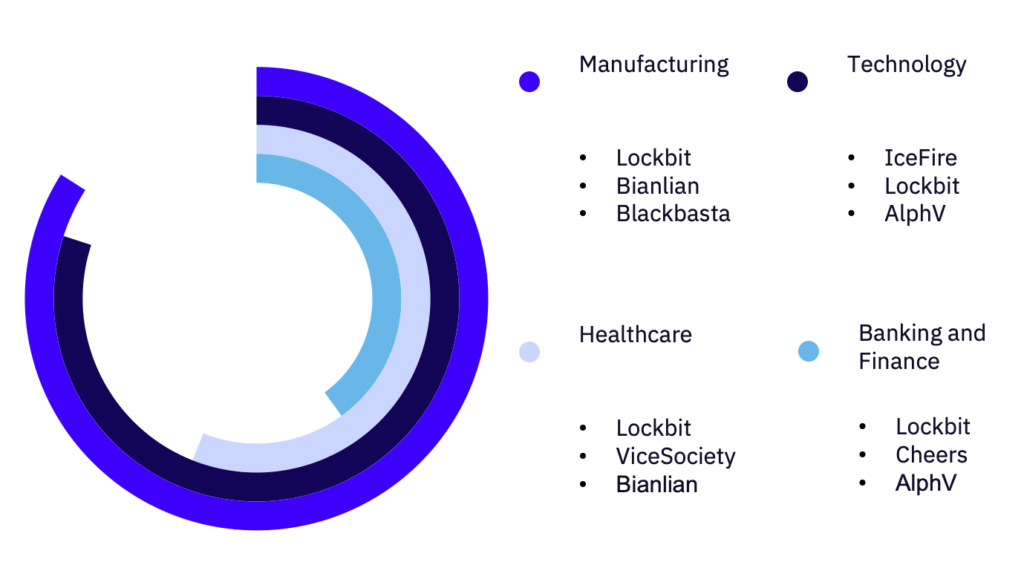
The Manufacturing vertical has had an eight-month run in the top three, and this marks the second month in a row that Technology has been in the top two, and the fourth month it’s been in the top three.
Among the top targeted industries, LockBit, IceFire, and BianLian were the most active groups, and the top countries targeted were the United States, Germany, Switzerland, and the United Kingdom. Notably, Technology and Manufacturing remain the top two most impacted verticals even when the US is removed from the data pool.
As August ended, several countries including Turkey–primarily due to IceFire victims–the United Kingdom, Germany, and the United States saw the biggest increase in overall targeting across all industries, while countries like France, Australia, Netherlands, and United Arab Emirates got a bit of a break with a decrease in ransomware victims.
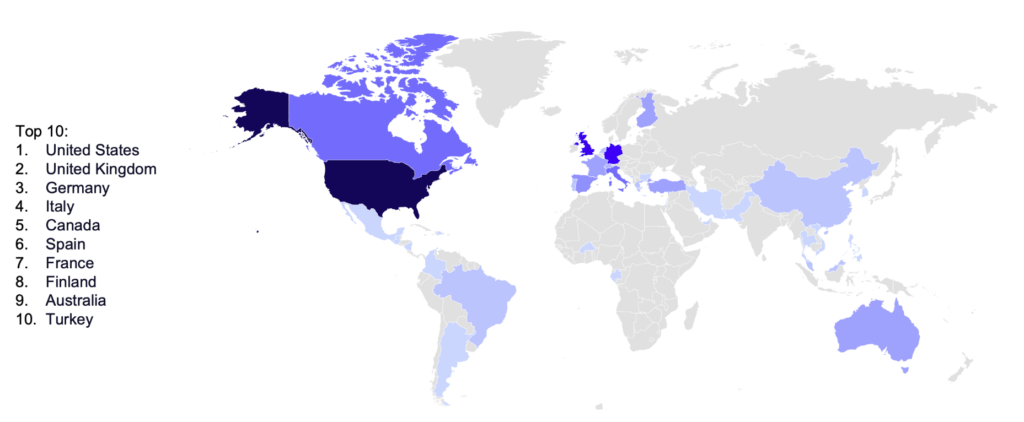
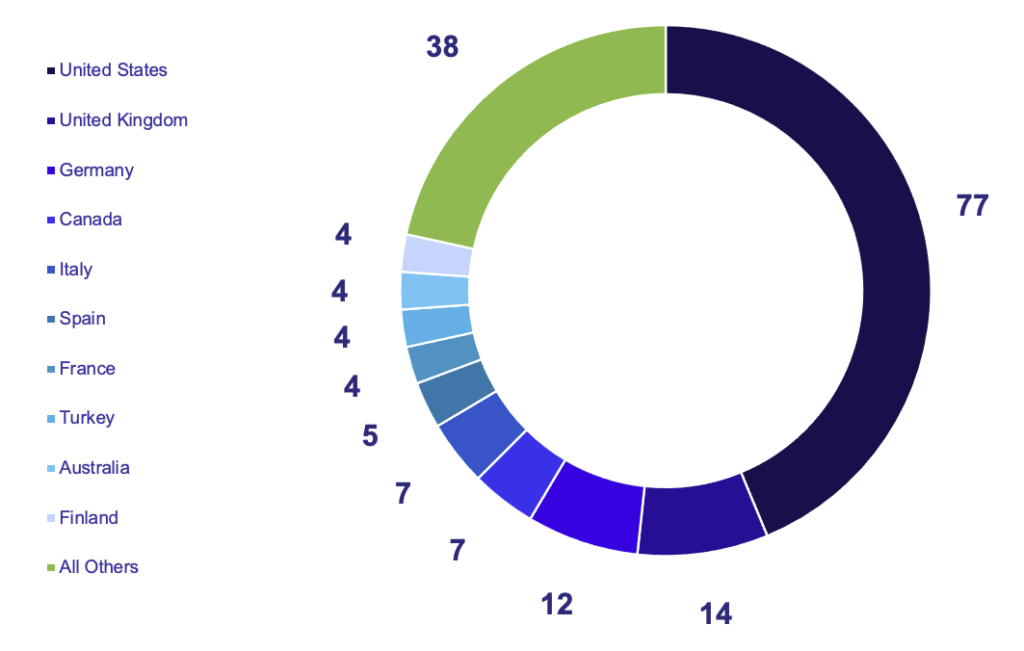
Overall, GRIT observed targeting against 35 of the 40 tracked countries in August. The United States represented 71.4% of attacks against the tracked industries, far more than any other country (the next most-targeted country is the United Kingdom with 17.1%). The groups most actively targeting the United States were LockBit, Blackbasta, and Bianlian.
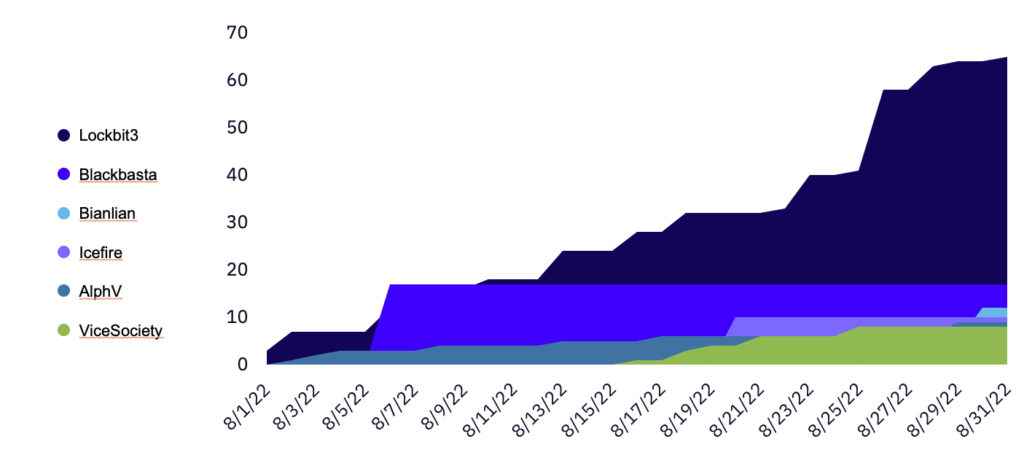
Lockbit continues to be the most prolific ransomware group by far, and their number of claimed victims per month continues to increase as 2022 progresses. Lockbit had an 8.3% increase in claimed victims from July to August, with 65 reports. Highlighting Lockbit’s dominance is Blackbasta, who took second place despite only posting on one day, with a total of 17 victims (a 22.7% decrease from July). Bianlian, a new contender as of July, took 3rd place with 12 total victims claimed in the last three days of the month.
Threat Actor Spotlight: IceFire Ransomware Group
IceFire was first noticed by the MalwareHunterTeam researchers in March of 2022, and at the time they didn’t utilize a leak site. In August, IceFire began double extortion operations using a leak site, with over 40 victims already included on the site on its first day of operation. Around the same time, BleepingComputer forum posts requesting help with IceFire ransomware began to pop up.
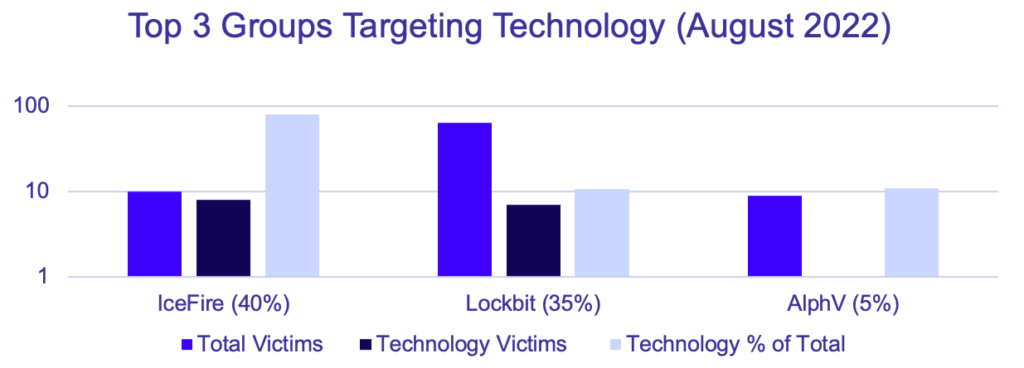
IceFire’s publicly disclosed victims are heavily focused on the Technology industry, and represent uncommonly targeted countries including Turkey, Iran, Pakistan, and the United Arab Emirates.
Notably, they have recently added a “Make a proof” feature, wherein victims can make a payment of exactly 1 XMR in order to decrypt a single file as proof that the group can decrypt encrypted files. This is an extremely uncommon tactic, as most sophisticated ransomware groups will normally provide proof by decrypting small files for free.
Other Notable Ransomware Groups
Donut Leaks

Donut Leaks was first observed in August attempting to extort victims from multiple industries and countries.
Their reported victims match the victim profiles of other ransomware organizations, suggesting a possible connection between affiliates in multiple groups attempting to gain additional revenue by threatening to release data separately from their affiliated ransomware group.
Final Thoughts
Overall, August appears to be a bit slower in broad-scale activity among established ransomware groups. Lockbit remains the most prolific ransomware group and maintains a strong lead among threat actors, with 8% more monthly reported victims in August. Alternatively, Hive, AlphV, and Blackbasta all saw large drops in total reported victims, dropping 73%, 57%, and 23% respectively from July to August.
Among targeted countries, 17 countries targeted in July were not targeted in August, including countries across Europe, Africa, the Middle East, and East Asia. Alternatively, 16 countries not targeted in July were targeted in August. These shifts suggest that many victims are targets of opportunity for affiliates across various ransomware groups.
Despite the slow-down in August, 2022 is likely to continue with ransomware being one of the most impactful threats that organizations face. As we roll into September, and the close of Q3, GRIT will continue to monitor for new trends in eCrime and ransomware.