
GRIT Ransomware Report: August 2023
Additional contributors to this report: Jason Baker, Ryan Silver
August’s trends in ransomware highlight that as much as the ransomware environment changes, it also stays the same. While at first glance August’s statistics reflect a 25% decrease in total observed victims, the removal of Clop’s mass campaign victims across the past two months results in a different picture, in which the total victims across other groups modestly increased or remained constant month-over-month. Separately, we observed a notable decrease in the diversity of active ransomware groups, with only 25 unique groups observed posting victims in August compared to 36 in July. Whether this reflects a lull in the operations of several Emerging groups or the short life cycle of Ephemeral groups will become clearer in the coming months. Regardless, the most Established ransomware groups remain resilient.
Geographic distribution of impacted countries shifted slightly this month, with Germany accounting for 6% of all observed attacks, and the United States accounting for a relatively low 41% of victims. While western Europe accounts for many non-US attacks, the region generally enjoys lower rates of ransomware and ransom payment, due in part to GDPR regulations that make ransom payments for “silence” less palatable and practical. Continued increases in western European attacks would mark a notable shift in ransomware’s global impact.
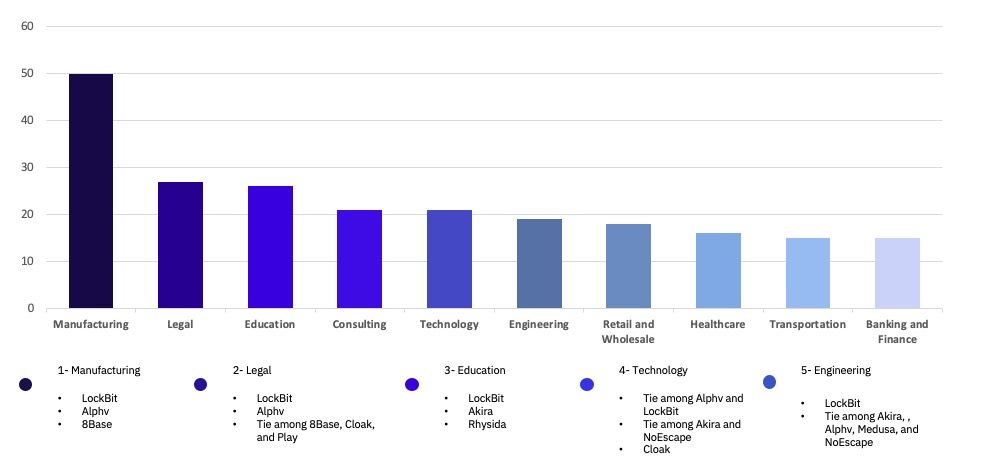
In terms of impacted industries, Manufacturing remains the most affected by ransomware, and we observed increases in total victims in the Legal, Education and Consulting industries. The technology industry experienced a substantial decrease in observed victims of 57%.
Following a noted slowdown in operations over the past 3 months, LockBit’s August “comeback” stands out, with the group claiming its second-highest number of monthly victims to date, second only to the number of observed LockBit victims in February 2023. This return to the top of the leaderboard could reflect a resumption of normal operations, overcoming of technical setbacks and issues, or a concerted effort to display group strength after rumors of internal strife circulated in security reporting.
This month’s threat actor spotlight focuses on the Developing group, Rhysida, which claimed high-profile victims in August and demonstrated a strong impact on victims in the healthcare and education industries. Rhysida’s focus on these industries has led to suspicions of operator overlap with Vice Society, an Established group which has similarly targeted education and healthcare and has posted no new victims since Rhysida’s emergence.
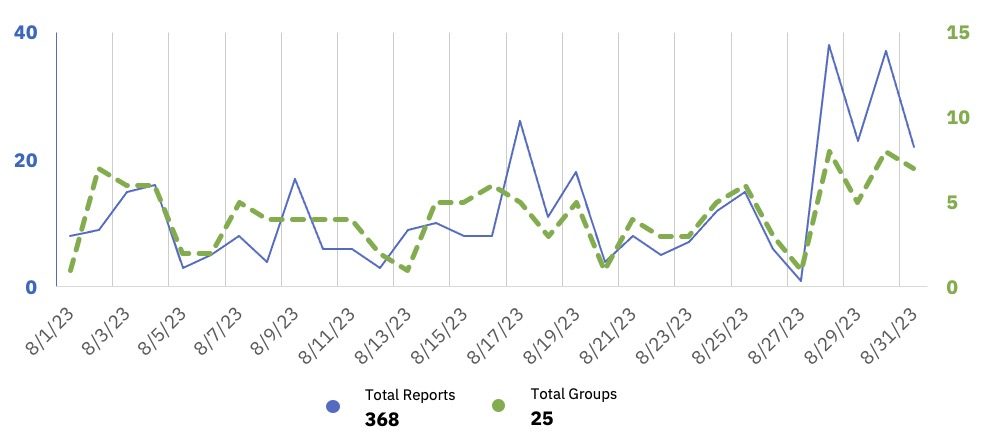
| Total Publicly Posted Ransomware Victims | 368 |
| Number of Active Ransomware Groups | 25 |
| Average Posting Rate (per day) | 11.9 |
Ransomware Trends
GRIT observed a 25% decrease in total observed victims from July to August 2023, but we note that this decrease is heavily impacted by victims of Clop’s MOVEit campaign, many of which were posted in July despite the attacks taking place in June. However, if we account for this skew by excluding the 171 observed victims claimed by Clop in July, we instead observe a 15% increase in victims attributed to other ransomware groups from July to August.
Overall, the total observed victims in August 2023 represent a 79% year-over-year increase relative to August 2022.
The final days of August saw multiple groups posting a high number of victims, including the Established ransomware group LockBit and the Emerging group Cloak, which posted 23 victims on August 28th.
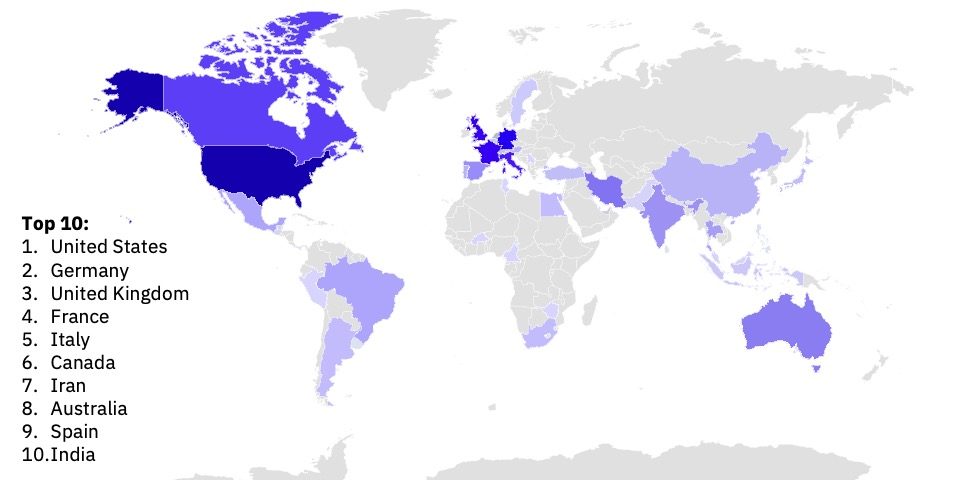
Ransomware Victims by Country
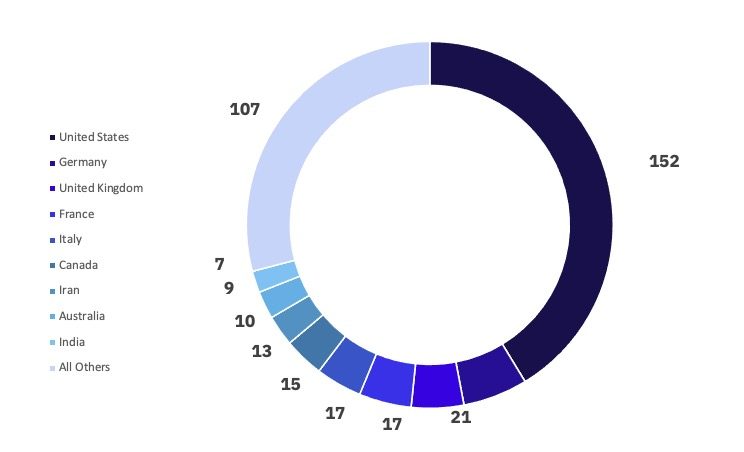
The United States remained on the receiving end of the most ransomware attacks in August, representing 41% of all observed attacks, or seven times the number of observed attacks against the second-most attacked Germany.
Attacks against US organizations are disproportionately attributed to LockBit, which is responsible for nearly 1 in 3 observed attacks against US-based organizations. Akira and Alphv also drive outsized impacts on U.S. organizations, accounting for 17% and 16% of attacks, respectively.
GRIT observed a 50% increase in victims from Germany between July and August, an increase mostly attributed to LockBit and the Emerging ransomware group, Cloak. August presents the second-highest victim count observed in Germany this year at 21, just short of March 2023’s 23 victims.
Iran’s presence on the list of most impacted countries is anomalous and can be attributed solely to posts by the Arvin Club, a seemingly Iranian group alternately described by themselves and researchers as a hacktivist group, an extortion group, and a ransomware group.
Ransomware Victims by Industry
Among the most heavily attacked countries, ransomware groups impacted the following number of distinct industries in each country:
United States: 27
Germany: 11
United Kingdom: 9
France: 11
Italy: 9
Among the most heavily attacked countries, the most impacted industries saw slight deviation from the norm. Manufacturing remained at a top spot, but the Legal, Education, and Consultant industries saw a relative rise in victims. This change also saw the anomalous decrease in victims within the Technology industry. The education industry was most heavily impacted by LockBit and Akira, which accounted for 57% of the education industry’s victims.
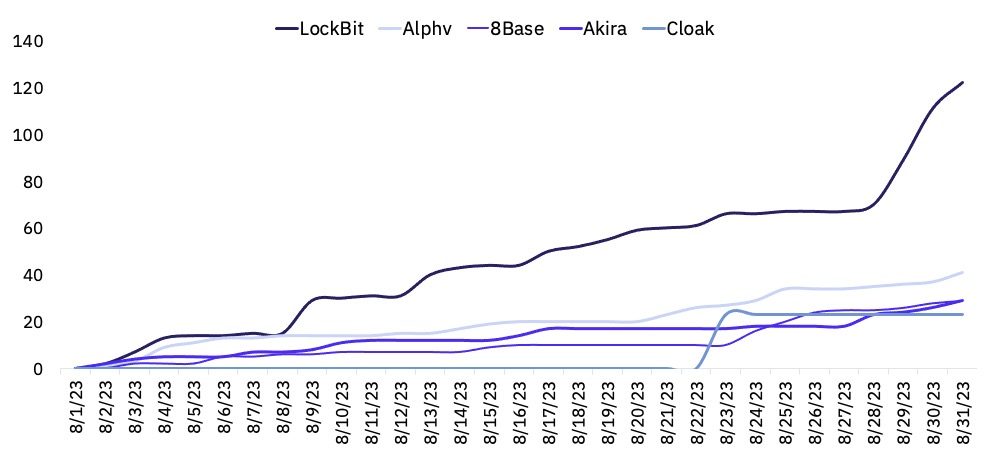
Cumulative Victims by Threat Group
The top three most active groups overall were Lockbit, Alphv, and 8Base. Both LockBit and Alphv are Established groups according to the GRIT Ransomware Taxonomy, while 8Base is still classified as an Developing group.
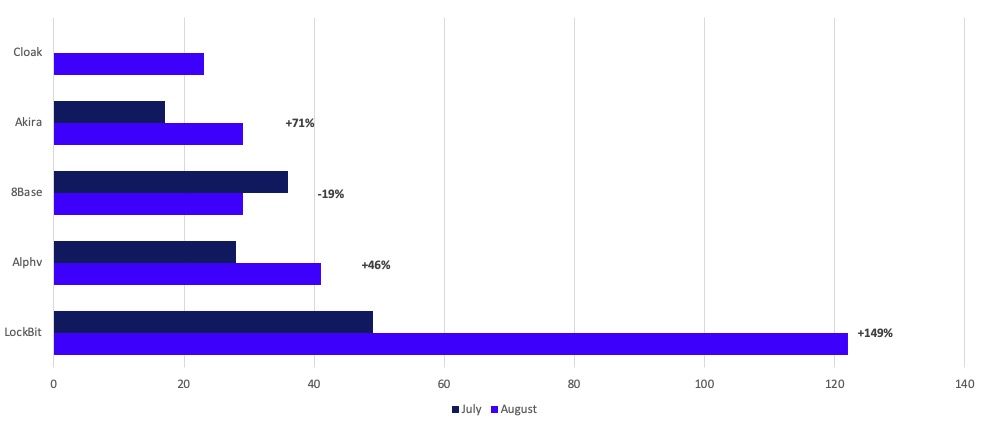
Following a decrease in victims over the preceding three months, LockBit went on to claim more victims in August than in June and July combined. August has been LockBit’s second-most active month in terms of observed victims, second only to February of this year.
Alphv retains its position as a leading ransomware group as it has throughout 2023. Alphv experienced a modest increase in observed reports from 28 in July to 41 in August, a 46% month-over-month increase and a 21% increase over its monthly average of 34 victims.
Since reporting a tranche of backdated victims in May 2023, 8Base has remained a top performer in the ransomware space, though its victims have decreased month-over-month. August continued this trend, with a 24% decrease in observed victims.
Threat Actor Spotlight: Rhysida (Developing)

Having first appeared in May and first posted victims in June of 2023, Rhysida is categorized by GRIT as a Developing ransomware group. Our categorization is based on Rhysida having continued operations in excess of three months, its Ransomware-as-a-Service (RaaS) operations, and its use of dedicated infrastructure to support data posting and victim communications.
Rhysida operates as a Ransomware-as-a-Service (RaaS) operation and practices “double extortion”; In double extortion attacks, system encryption is paired with data exfiltration, allowing the attacker to threaten the publication of sensitive data in instances where victims would otherwise choose not to pay ransoms for decryption.
Rhysida has attracted attention during its short existence through high-profile attacks, including impactful attacks against healthcare and educational institutions, two industries that are often restricted or avoided by ransomware groups to avoid increased law enforcement pressure. Rhysida has attacked numerous public and private educational institutions since their emergence, including universities and school districts. Victims in the education sector account for 35% of the group’s victims so far.
In August, Rhysida claimed responsibility for a high-impact attack against a large US healthcare company, allegedly resulting in stolen patient records and social security numbers. The attack resulted in shutdowns of hospital IT networks, forcing the victim organization to revert to paper records until the incident was contained.
Like most ransomware groups, Rhysida has most frequently impacted organizations based in the United States and Western Europe. However, Rhysida has also attacked Latin American victims, including a June attack impacting the Chilean Army.
Researchers at Check Point have noted similar tactics, techniques, and procedures (TTPs) between Rhysida and Vice Society, an Established ransomware group with a similar history of impacting healthcare and educational institutions. Check Point notes that Vice Society historically deployed multiple forms of commodity ransomware, suggesting that some former Vice Society operators may be using Rhysida, rather than Rhysida representing a Rebrand of Vice Society.
- GRIT notes that Vice Society operations have appeared dormant since June 2023, when Rhysida victims began, suggesting a potential Splintering or operational pause by Vice Society.
Rhysida’s attack tactics include the use of phishing emails for initial access, followed by the deployment of Cobalt Strike for lateral movement. Rhysida’s ransomware is typically deployed through PowerShell scripts executed via PsExec, and their ransomware appends the “.rhysida” file extension to affected files and leaves a PDF ransom note titled “CriticalBreachDetected.pdf” on impacted systems.
Other Notable Ransomware Events
The FBI Takes Down Qakbot
On August 29, 2023, the U.S. Attorney’s Office announced a successful operation resulting in the disruption of the Qakbot (aka QBot) malware botnet. The FBI was able to access Qakbot’s infrastructure and redirect the botnet’s traffic for over 700,000 victims to infrastructure controlled by the FBI. After gaining access, the FBI turned Qakbot’s features against itself, issuing an uninstaller file that “untethered” victim machines from the botnet.
The Qakbot disruption will likely negatively impact ransomware operations in the future, including those of Black Basta, some of whose affiliates have historically utilized Qakbot for initial access in intrusions. Though Black Basta’s affiliates have used other initial access methods, the removal of Qakbot lessens the diversity of options for affiliates and other groups.
This takedown and its fallout is likely to mirror that of the Emotet takedown in January of 2021, in which federal law enforcement was able to disrupt Emotet’s botnet that had infected over 1.6 million devices across the globe. Although the takedown caused a clear setback for Emotet’s operators, Emotet was able to reestablish a botnet the following year and resumed infecting devices. GRIT assesses that Qakbot operators will likely follow suit, with an observable period of downtime followed by an eventual resurgence.
LockBit Returns to Form
GRIT observed a substantial decrease in victim posts from the Established ransomware group, LockBit, in recent months, a trend which ended in August. The group saw its second most successful month since inception, amassing 122 observed victims, just short of February 2023’s record of 127 victims. We note that the group’s victim count of 62 and 49 during June and July 2023, while low compared to the immediately preceding months, is still comparable to LockBit’s victim counts from June and July of 2022 (44 and 60, respectively).
This renewed uptick in activity comes on the tail of Analyst1 reporting indicating potential troubles within the group that may have contributed to LockBit’s decreased summer performance. Leadership turmoil and difficulty hosting large amounts of stolen data were two issues explored within Analyst1’s reporting, which mirror growing pains experienced by legitimate organizations during periods of rapid growth. GRIT observed problems with downloading data from LockBit’s data leak site and apology posts for an “unauthorized” attack against a child’s daycare, which supports claims in Analyst1’s report.
Ransomed[.]vc Solicits Affiliates, Posts Victims on Clearnet
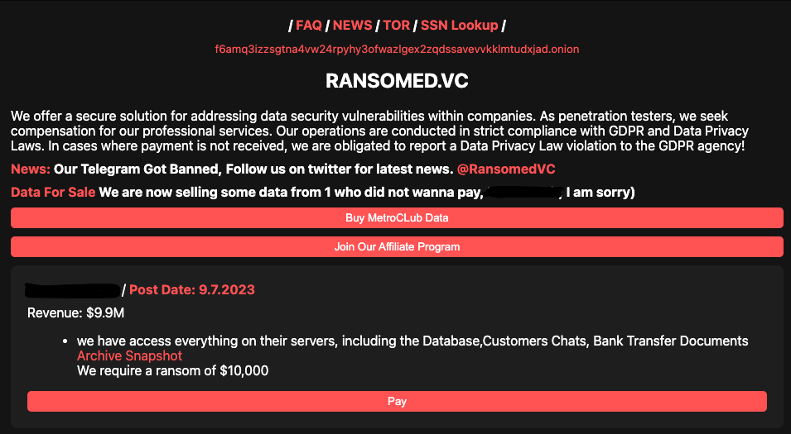
In August, an alleged ransomware group calling themselves “Ransomed” registered and opened a clearnet website, ransomed[.]vc, and began soliciting affiliates for ostensible ransomware operations (described as “penetration testing” on the site, a commonly used euphemism in the ransomware ecosystem) The group also appears to leverage a Twitter/X account, following the banning of its Telegram channel.
As of early September, the group appears to have listed 21 “victims”, though provided details include likely previously compromised data, potentially public data, and two instances claiming site defacement. In two instances, the group claims to have collaborated with the Everest Ransomware Group in compromising victim networks.
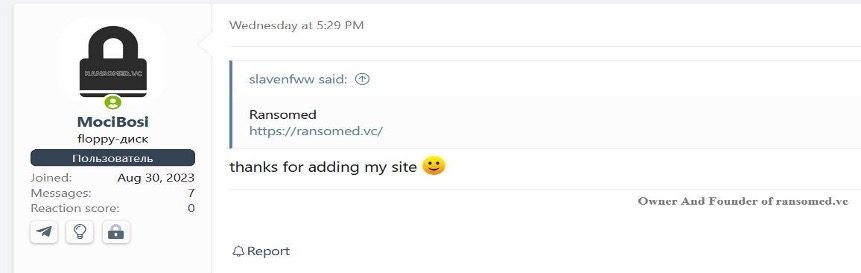
The group also appears to have a potential owner active on the dark web forum XSS. On August 30, the user MociBosi posted “thanks for adding my site 🙂” on a thread containing links to many other ransomware data leak sites, in response to another user providing a link to the Ransomed clearnet site. Separately, MociBosi replied to a post by LockBit’s spokesperson account on the forum, which translates to “I have ransomed dot vc, there is also an affiliate program, most of the people that come to us are people who weren’t enough to join lockbit3 hahaha”. These posts could reflect internal recognition of the group’s “newcomer” status and relative operational immaturity.
The use of a clearnet page is likely an attempt to increase the group’s visibility and brand recognition, and to put pressure on victims to comply. This approach follows Clop’s use of clearnet pages and torrents to post and distribute victim data in the wake of a recent mass exploitation campaign. We assess that additional ransomware groups will attempt to leverage some form of clearnet pages for similar purposes in the future.
Clop’s MOVEit Campaign Likely in Closing Stages
As of Mid-August, GRIT has observed a seeming end to Clop’s (Stylized as Cl0p) gradual posting of victims associated with its mass exploitation of the MOVEit managed file transfer application. Clop had posted victims incrementally since late June, possibly in an effort to gradually process the large volume of impacted victim data. Observed movement on Clop’s data leak site from late August on appears to reflect administrative actions such as posting remaining victim data, and we assess that additional victims are increasingly unlikely as the group finishes or terminates any remaining negotiations. Based on historical behavior and TTPs, Clop will likely enter a period of relative dormancy until its next attempted mass exploitation campaign.
Akira Ransomware Exploits Cisco VPN Vulnerabilities for Access

Akira, a Developing ransomware group first seen in March, has been observed by security researchers as targeting Cisco Virtual Private Network (VPN) products to gain initial network access in attacks since March 2023. In observed attacks, Akira obtained authenticated access to Cisco VPN environments without Multi-Factor Authentication (MFA) enabled, either through compromised credentials (credential stuffing) or brute-force attacks. The prevalence of Cisco VPN solutions in corporate environments has probably allowed for Akira to pursue non-alerting probing and attacks by volume, but this access method can be mitigated through mandatory MFA enforcement.
AnonFiles Shutdown Impacts Ransomware Groups
The anonymous file-sharing service, AnonFiles, was shut down in August following termination of service by the site’s proxy provider due to a high volume of abusive content. AnonFiles was known in part for its use by ransomware groups to exchange data with victims and, in some cases, to mirror leaked victim data. Following the site’s shutdown, the ransomware group 8Base acknowledged that it had lost most of their victim file links as a result. The impact of AnonFiles’s shutdown on 8Base and potentially other groups highlights the recurring issue of mass file storage by successful ransomware groups, who must often find redundant and reliable means of hosting enormous amounts of data for download. We assess that file storage and victim data availability will continue to pose an issue for ransomware groups in the short- to mid-term.
Multiple Extortion and Leak Groups Reemerge Following Dormant Periods


GRIT has observed the resumption of ransomware and leak operations over recent months from the Cuba, Donut Leaks, and Arvin Club groups, having last posted victims in April 2022, December 2022, and October 2022, respectively.
- Cuba is a conventional double-extortion ransomware group first observed in late 2019.
- Donut Leaks is a data extortion group previously reported as associated with ransomware groups including Hive and Ragnar Locker; conflicting reporting describes the group as an extortion-only associate of ransomware group or as a distinct RaaS affiliate.
- Arvin Club claims to be an Iranian Hacktivist group, often described in reporting as a ransomware group, and has historically posted leaked data from Iranian targets through Telegram.
The resumption of operations for each of these groups highlights the frequency with which cybercrime group hiatuses occur, often for the purpose of “cooling off” from increased law enforcement pressure. Prolonged operational pauses can complicate the effective classification of ransomware groups; incomplete information prevents confidence in definitive classifications of “Defunct” groups, and GRIT’s ransomware taxonomy avoids assigning such a classification except in instances of clear Rebranding or Splintering into subsequent groups. Analysis of ransomware and extortion group behavior and TTPs following ostensible “re-emergence” will also aid determination of continued group composition to determine potential instances of group names being “co-opted” or repurposed by other groups.
GRIT currently assesses that the re-emergence of these three groups probably does not portend an increase of dormant ransomware group reemergence in the short term, based on the relatively low impact and ingenuity of each group, as well as the continued availability of other competitors in the ransomware and data extortion space.
New Ransomware Groups Tracked by GRIT in August 2023:
Cloak (Emerging)
The Emerging ransomware group Cloak posted 23 mostly European Small- to Medium-sized Business (SMBs) as victims on August 28th, 2023. This bulk posting of victims could suggest that Cloak’s operations began prior to August.
Of the 23 posted victims, 21 were subsequently marked on Cloak’s data leak site as “Data Deleted”, potentially indicating a high rate of successful payment or issues with posting victim data. We note that retaining the names of victims on a data leak site post-payment is anomalous, with most ransomware groups removing any trace of victim identification in exchange for payment.
INC Ransom (Emerging)
INC Ransom posted three victims throughout August, with operations seemingly continuing into September. Observed victim posts are scattered across multiple dates, with approximately 12 days passing in between each posting, potentially indicating a relatively immature Emerging group. Of note, INC ransom maintains a dedicated data leak site and a “feedback” form.
Metaencryptor Team (Emerging)
The “Metaencryptor Team” claim on their blog to be “a group of young people who identify themselves as specialists in the field of network security with at least 15 years of experience.” During the month of August, the group posted 11 victims, though the dates for each victim are inconsistent and are backdated at least a year. The initial “about” message on the group’s home page is dated as January 20, 2022, suggesting that the group may have delayed posting victims during its early operations.
Of note, 36% of the group’s victims are based in Germany, and only 9% of the group’s victims are U.S-based, an anomalous distribution in the ransomware space.
Final Thoughts
August shows the continued success of Developing and Established ransomware groups and their resilience despite lulls or pauses in operational activity. Our statistics this month also highlighted the importance of context in our analysis; a seeming decrease in total observed victims can be more accurately and helpfully reviewed as an objective increase for most groups, with data skewed by the TTPs of a single unique group. Current and future analysis demands that ransomware activity be assessed in the context of the entire ecosystem and wider timeframes.
August’s trends show several hallmarks remaining the same – Manufacturing stays the most impacted industry; the United States stays the most impacted country. But alongside this consistency are changes to secondary victims – Western European countries ebb and flow across our “Top 10” list, and multiple industries experience increases and decreases month-to-month. These shifts are likely driven by both opportunistic attacks by ransomware groups as well as surges from groups that disproportionately impact specific sectors, such as Rhysida’s driving of increased education and healthcare victims.
Much attention will likely be paid to LockBit in the coming months as researchers work to determine whether its surge of victims in August is a temporary correction from underperforming months or a return to form that is likely to continue. While the group’s 122 victims in August is substantial, it does not represent a giant leap forward for the group, and we do not yet know if the group has fully overcome previously reported issues that impacted its summer operations. These assessments aside, the group’s performance points to a truth in characterizing ransomware groups: short-term setbacks and fluctuations are not necessarily reliable indicators of long-term performance and sustainability.
GRIT continues to monitor the performance and longevity of Emerging groups to separate short-term Ephemeral groups from what will become Developing groups. We note that new groups such as Ransomed typically reduce barriers to entry for less experienced or skilled operators and that such groups often bring new TTPs that may be integrated or normalized over the wider ecosystem with time. While Ransomed may seem an outlier for soliciting affiliates on the clearnet today, the approach could become commonplace should the group find success in the coming months.
In conclusion, Ransomware operations continue to increase in aggregate, demonstrating year-over-year growth that we assess will continue through the end of 2023. As formerly “taboo” victims such as education and healthcare are increasingly victimized over time, we may see an increased normalization of this attack behavior, particularly if attacks against these sectors fail to generate substantial pressure or deterrent efforts by law enforcement.
The GRIT Ransomware Taxonomy
By subdividing ransomware groups, GRIT can obtain more detailed insights into how ransomware groups progress in their level of operational maturity and can classify and identify potential rebranding activity.
We distinguish ransomware groups by placing them into these six categories:
EMERGING
This category is reserved for new ransomware groups within their first three months of operations. These organizations may be short-lived, resulting in an Ephemeral group; may be determined to have Splintered or Rebranded from an Established group; or may move on to further develop their operations and TTPs over time.
EPHEMERAL
These groups are short-lived, with varied but low victim rates. Observed victims are usually posted in a single or short series of large postings rather than a continuous flow over time. Ephemeral groups, by definition, terminate operations, spin-off, or rebrand within three months of formation. These groups may or may not have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
DEVELOPING
These groups have conducted operations for three months or longer, resulting in a recurring flow of victims. Developing groups do not appear to be directly linked to other ransomware groups as a Splinter or Rebrand but may include some experienced ransomware operators. Developing groups generally improve their people, processes, or technology over time by recruiting additional members, refining TTPs, or improving the quality of their associated ransomware and encryption. These groups generally have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
SPLINTER
These groups consist of a plurality of members from previously Developing or Established groups and may have formed either by choice or due to exclusion. These groups may be identified by very similar or overlapping TTPs and tooling or through HUMINT gathered through interactions with personas on the deep and dark web. Splinter groups differ from Rebrands by the continued existence of the original organization as the Splinter group operates.
REBRAND
These groups consist in whole, or in part, of former Developing or Established groups. Rebrands often maintain the same people, processes, and technology as the original group. Rebrands are generally undertaken in order to minimize attention from law enforcement or intelligence officials or to avoid negative publicity.
ESTABLISHED
These groups have operated successfully for at least nine months and have well-defined and consistent tactics, techniques, and procedures. Established groups often possess functional business units that enable sustained ransomware operations, with specialists focused on areas such as personnel, encryption, negotiations, etc. These organizations successfully employ technology and redundant infrastructure to support their operations.
There are multiple routes a group can take through the various classifications, and no one route is standard. While one group may begin as “Ephemeral” and move their way through the ranks to “Full-time,” another group may enter as a “Rebrand” as part of a larger obfuscation strategy to avoid attention from law enforcement.

