
GRIT Ransomware Report: May 2022
The GRIT Ransomware Report Emerges
In April of 2022, the GuidePoint Research and Intelligence Team (GRIT) released a white paper outlining ransomware trends in Q1 2022, how they compare to trends from 2021, and discussed how threat intelligence can be a huge asset for improving and sustaining effective cyber defense operations in organizations across all industry verticals. We received a lot of positive feedback from peers and clients about how useful the white paper was for keeping a pulse on the most current ransomware trends and, thus, the GRIT Ransomware Report has emerged.
The goal of GRIT’s Ransomware Report is to provide a consolidated overview of ransomware trends, focusing on changes to targeting methodologies, TTPs/IOCs, and/or new additions to the ransomware scene, including notable or suspected rebrands. Ransomware has demonstrated time and time again that it is here to stay and with cyber threat intelligence moving at an ever-increasing pace, we need a way to keep our finger on the pulse. The GRIT Ransomware Report is our way of staying up to date on emerging ransomware trends and developments and regularly sharing it with the community.
Moving forward, GRIT will produce monthly blogs summarizing recent ransomware trends and highlighting new and emerging ransomware threats. We also plan to release quarterly and annual reports that have a larger and more in-depth review of ransomware trends across all industry verticals. Whether you are using these reports for strategic, operational, or tactical threat intelligence, the GRIT Ransomware Report is a great place to keep your finger on the pulse of ransomware intelligence.
Ransomware Trends
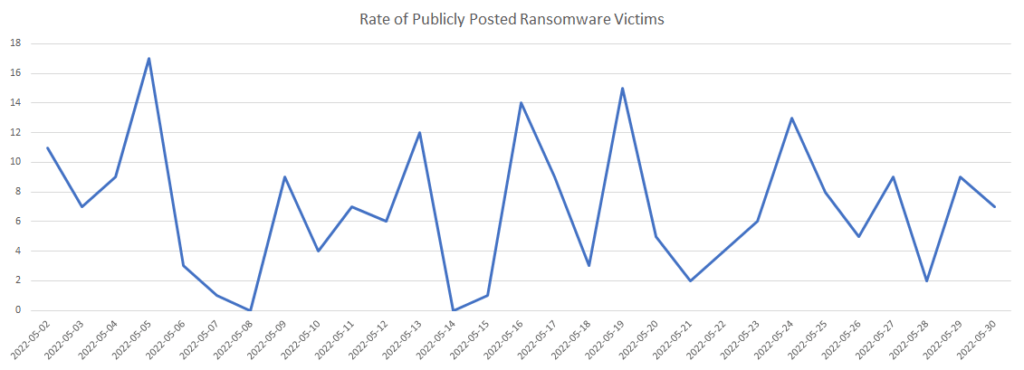
May brought us similar trends to what we have seen month over month so far in 2022. With over 200 publicly posted ransomware victims from 21 active ransomware groups, signs continue to point to ransomware ramping up as we approach the end of Q2. The average rate of publicly posted ransomware victims was more than six victims per day with a large majority of ransomware victims posted by the Lockbit ransomware group.
| Total Number of Public Ransomware Victims | 205 |
| Number of Active Ransomware Groups | 21 |
| Average Number of Publicly Posted Victims per Day | 6.61 |
During the course of May, there were only two days where there were no new ransomware victims posted publicly while there were six days that had 10 or more publicly posted ransomware victims. Overall the last 30 days of ransomware activity continue to show the high levels of operations conducted across all ransomware groups.
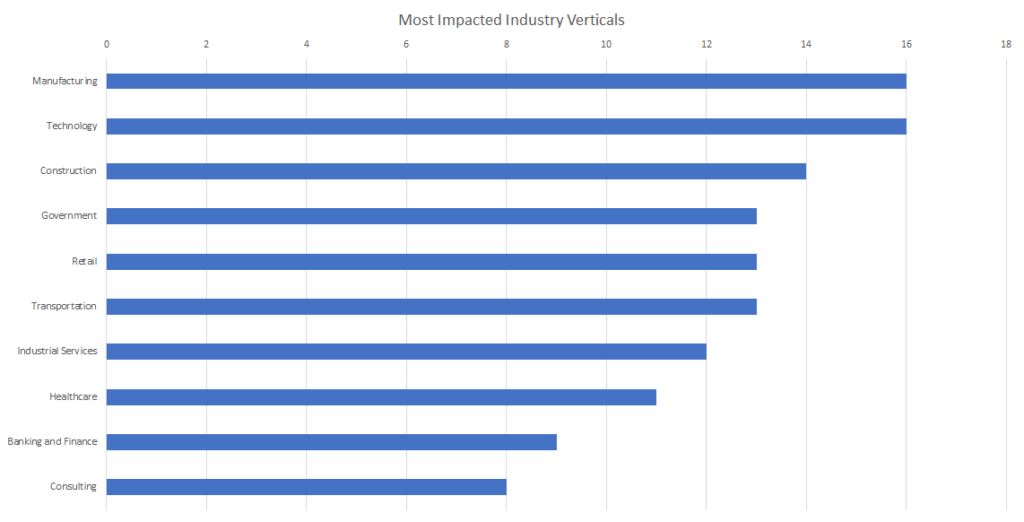
The manufacturing and technology sectors were impacted the most during May with the construction, government, and retail sectors close behind. Other critical infrastructure sectors in this month’s top 10 most impacted industries include transportation, healthcare, and banking & finance.
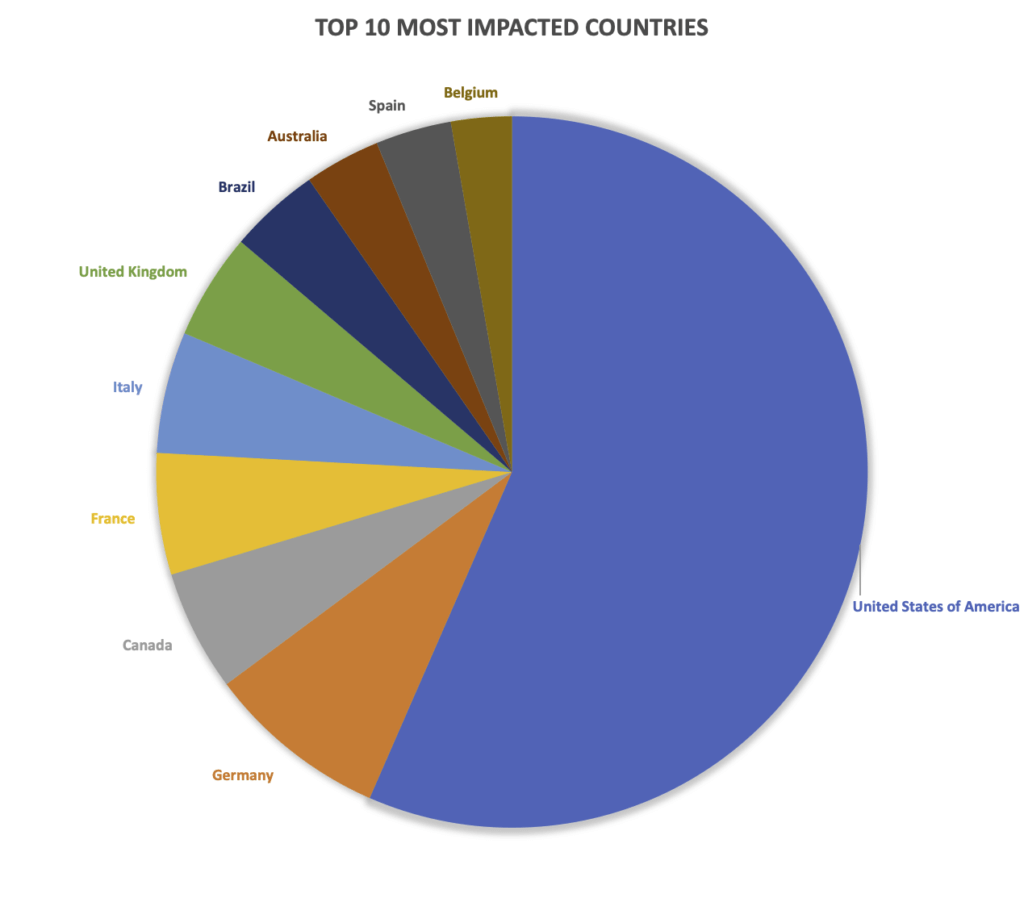
Unsurprisingly, the United States was the most targeted and continues the trend of being the most impacted country in 2022. With 82 publicly posted ransomware victims, the United States comprised 40% of the total ransomware victims for May. Also unsurprisingly, eight of the nine remaining countries in the top 10 are all western countries.
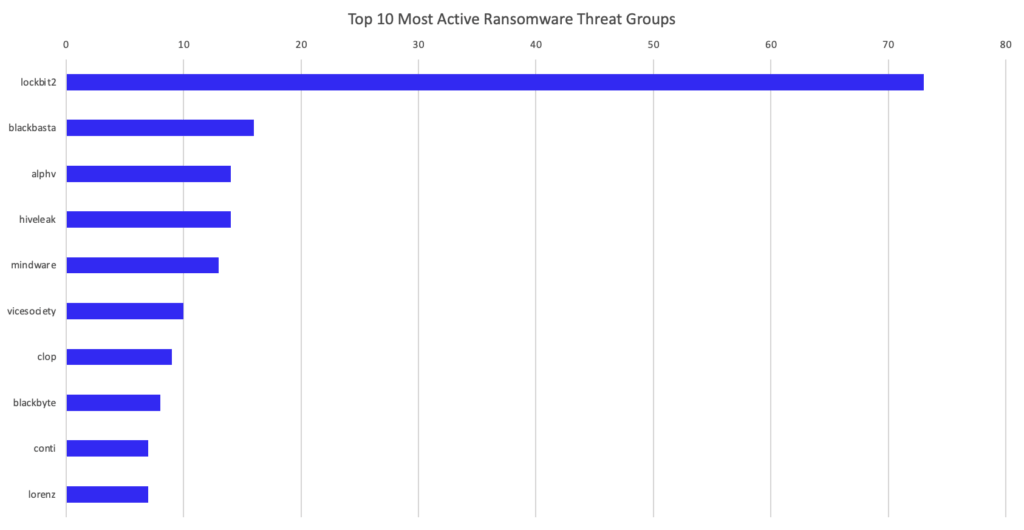
Lockbit was yet again the most impactful ransomware group in May with 73 publicly posted victims. Blackbasta, a relatively new player in the ransomware space, AlphV, Hive, and Mindware ransomware groups were also observed to have more than 10 publicly posted ransomware victims during this month’s analysis.
Threat Actor Spotlight: Lockbit
Lockbit continues to lead ransomware groups month over month in the number of publicly posted ransomware victims. Lockbit posted 73 public victims in May 2022 while the next most active ransomware group in May, blackbasta, only published 16. Based on their posting rates so far in 2022, it is unlikely that Lockbit will slow down any time soon.
Vx-Underground posted a tweet on May 23 indicating that the newest version of Lockbit, version 3.0 and rumored to be called “Lockbit Black,” has been released and is available within the groups affiliate panel. With intelligence reports suggesting that affiliates from groups such as Evil Corp are now moving to use off-the-shelf ransomware such as Lockbit, it is unlikely that Lockbit will be going anywhere soon.
Other Notable Ransomware Additions and Rebrands
New Ransomware Group: Blackbasta
We are going to break our own rules here and bring in our first notable mention from the end of April 2022. Blackbasta recently ended up on threat intelligence radars at the end of April when they began posting public victims to their leak site. Since then, Blackbasta has quickly risen to the number two spot for the number of public victims posted for May 2022.
Some researchers are speculating that blackbasta may be a rebrand of, or at the very least have a very strong relation to, Conti.
New Ransomware Group: Cheers
A new ransomware group has emerged that calls itself Cheers, or Cheerscrypt, ransomware. This ransomware family has been observed targeting VMware ESXI servers, a tactic more commonly observed from Lockbit, RansomExx, and Hive. Targeting ESXI servers allows the threat actor to encrypt multiple virtual machines through the encryption of the virtualization host thereby having a large impact on the victim’s virtual environment.
New Ransomware Group: Industrial Spy
Industrial Spy is a relatively new data extortion marketplace that previously focused on allowing threat actors to purchase data stolen from companies, however, it looks like the forum’s owners may be pivoting their business model. MalwareHunterTeam recently discovered a change to the Industrial Spy malware that looks to be making a potential change to focus on conducting ransomware operations. Intelligence reports speculate that the Industrial Spy ransomware may have strong ties to Cuba ransomware, however, it is unclear whether the relations to Cuba are the result of testing ransomware operations or if it is part of a true rebrand.
Conti Supposedly Closes Up Shop
According to intelligence reports, it is rumored that Conti is going to be closing down operations in favor of a rebrand to several smaller ransomware groups that are already well established and operational including Karakurt, AlphV, Hive, and Blackbasta.
Conti has been under scrutiny over the past few months for their messaging around the Ukraine/Russia conflict, open threats to the Costa Rica government, and multiple high-profile victims. Despite their infrastructure going offline temporarily, the group has intermittently posted victims to their Conti News site since the reports of the rebrand surfaced. While this is rumored to be from past victims that are just recently being posted, it is clear that something is changing with the operations of the Conti Ransomware group.
Wrap Up
Ransomware groups are continuing to ramp up operations and rebrand when possible to stay under the radar. As we progress into June, we expect the trends to continue to ramp up into the end of Q2 2022. GRIT will continue to closely monitor and develop intelligence from over 20 active ransomware groups and, until next month, happy hunting!