
GRIT Ransomware Report: May 2024
Additional contributors to this report: Grayson North, Jason Baker
May 2024 closed with an increase in overall victim volume, though deep review reveals that the increase was driven disproportionately by LockBit’s 175 posted victims, accounting for 37% of the month’s total. LockBit’s administrator – “LockBitSupp” – was publicly identified by international law enforcement and sanctioned in early May, and this may have encouraged the group to proceed with emptying a backlog of victims – we do not assess with LockBit successfully attacked such a high volume of new victims in the course of a single month. Whether this bulk posting represents a “spring cleaning” or a “death rattle” remains to be seen in the coming months, as LockBit’s long-term viability after repeated law enforcement disruption becomes clear. We have already observed a shift in LockBit’s victim base towards non-US organizations, in a move that may signal early impacts of sanctions on LockBit’s ability to monetize US-based victims.
Two Established groups, Play and RansomHub, appear to be emerging as new leaders in the ransomware landscape, having increased their operational tempo relative to early 2024. Play has been within the top five most active groups since February 2024 and even rose to the top spot during April 2024. Despite only appearing publicly in February, RansomHub quickly rose to the ”Top five” in March and has gone on to become one of the three most prolific ransomware groups for the past two months; we assess this level of activity is likely to continue. We have covered RansomHub’s recruitment efforts on illicit forums in previous Ransomware Reports, and these efforts appear to be paying dividends.
May 2024 also saw the emergence of several new ransomware groups that have performed abnormally well when compared to historical norms. The emergence and success of new groups may be driven at least in part by the displacement of affiliates following Alphv’s nominal disbanding and law enforcement disruption of LockBit. Such disruption may encourage experienced affiliates with prior experience to seek new opportunities with lesser-known groups that offer better “benefits,” or even to “strike out on their own.”
May resulted in 33% increase overall in ransomware activity compared to April 2024. In 2023, we observed a similar increase month-over-month, with a 15% increase in May 2023 relative to April 2023, potentially indicating some degree of seasonality. We continue to observe year-over-year increases in the number of distinct ransomware groups operating, with the 38 unique groups claiming victims in May 2024 representing a 35.7% increase of May 2023’s 28 unique groups. This may represent increased dispersion of ransomware activity across a greater number of smaller groups, and away from large, monolithic groups such as Alphv and LockBit. Whether this dispersion is a short-term or long-term phenomenon remains to be seen and will likely be reflected in our metrics in the coming months.
| Total Publicly Posted Ransomware Victims | 475 |
| Number of Active Ransomware Groups | 38 |
| Average Posting Rate (per day) | 15.1 |
Ransomware Trends
During the early weeks of May, LockBit published a large batch of victims to their data leak site, resulting in a large spike of activity on May 9th. LockBit’s “dumping” of 76 victims on this date accounts for 16% of May’s total observed victims and 43% of LockBit’s claimed victims for the month.
We continue to see a correlation between total observed victim volume and the number of unique ransomware groups operating during a given month; the 38 unique groups observed claiming victims in May and the outsized performance of some newcomers likely contributed in part to May’s victim increases.
Interestingly, May’s trends reflect a more pronounced slowdown over the weekend. May 3rd, 12th, 19th, and 25th all resulted in one or zero victim posts, and each fell on a Friday, Saturday, or Sunday. Monday through Wednesday remain the days of the week during which most victims are posted to data leak sites.

Ransomware Victims by Country
LockBit’s claimed victims in May reveal a possible shift in the group’s targeting patterns following the imposition of US, UK, and Australian sanctions on May 7th. While the United States remains a significant target, the proportion of LockBit attacks targeting U.S. victims dropped post-sanctions by 24% compared to April 2024. Interestingly, the decrease in US victims applies more broadly, with the overall percentage of US-based organizations as ransomware victims decreasing across all groups by 10% from April to May.
May 2024 shows a more even distribution of reports across multiple countries compared to the April 2024 dataset. While U.S.-based organizations remain the most common victims (47.6%) in May, other Western nations including the U.K. (5.7%) and France (4%) account for a greater percentage of victims in May relative to April.
Notably, victim organizations in India and Spain both experienced a substantial increase in observed attacks, more than doubling from 4 to 15 and 6 to 16 victims respectively. This broader distribution across various regions could indicate diversified targeting or impacts of operations worldwide, particularly if the trend continues.


Threat Actor Trends

LockBit has seemingly reclaimed their status as the most active ransomware group based on the number of victims posted, but we note that this is heavily based on a consolidated “dump” of victims occurring shortly after sanctions were announced against one of LockBit’s administrators in early May. We do not know the extent to which LockBit’s victim posts in May represent new vs. previously unclaimed victims, but we do not assess that LockBit impacted 175 new victims in May.
Play continues to be a largely silent frontrunner among their peers. Despite a slight decrease in posts relative to April, their posts are largely consistent with preceding months. As GRIT has previously identified, Play continues to post victims in “batches” every 3-10 days.
RansomHub has rapidly “climbed the ladder” of ransomware groups in terms of victim volume since their public emergence in February 2024. The group claimed 27 victims in May, continuing an upward trajectory from 23 in April and 18 in March. We attribute this increase at least in part to an increase in experienced affiliates from other ransomware groups, based on public and internal reporting.

Threat Actor Spotlight: Hunters International (Established)
Hunters International is an Established Ransomware-as-a-Service (RaaS) group that has been operating since at least October 2023. The group’s affiliates employ double-extortion tactics against victim organizations and reported ransom demands have reached into the tens of millions, though we lack reporting on the frequency and amounts of final ransom payments. The group maintains an unusually sophisticated Data Leak Site (DLS) considering its length of operations, which may indicate the involvement of experienced operators, a Rebrand of another RaaS group, or Hunters’ functioning as a Splinter group from another RaaS group.
Researchers have noted an overlap between the code of Hunters International’s encryptor and that of Hive, as observed in open-source reporting, though we do not know the extent of any core or affiliate overlap between the two groups. The now-defunct RaaS group Hive was disrupted by law enforcement in January of 2023. In October 2023, Hunters International disputed any connection to Hive on their data leak site, stating that the code was merely purchased from Hive and that the codebase for Hunter International’s encryption malware has been updated to exclude the outdated Hive code. We cannot fully assess the validity of Hunter International’s claims that they are not related to Hive ransomware.
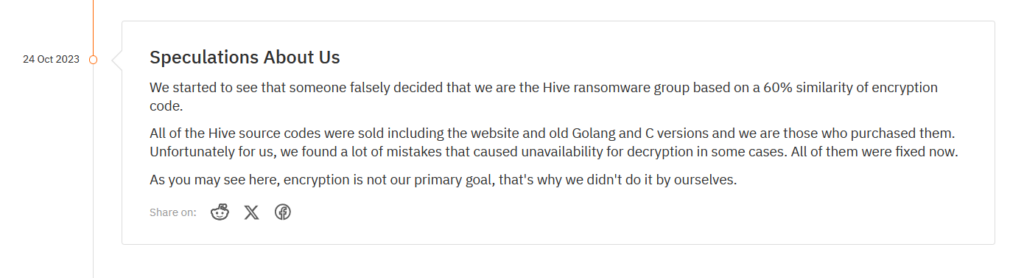
Hunters International likely streamlines the victim negotiation processes through a victim portal that matches the sophistication of the group’s data leak site. The portal is split into five sections: Overview, Disclosures, Decryptions, Payment, and Support, which handle aspects of an average ransomware negotiation. The “Overview” section of the victim portal lists basic details of the attack, including statements that files were encrypted, and that data has been exfiltrated from the victim’s network. Of note, the section contains a block that states “A bulk email will be sent to inform your customers, partners, employees, and competitors regarding the incident,” which implies that Hunters International may make third-party notifications as an escalated coercive action.
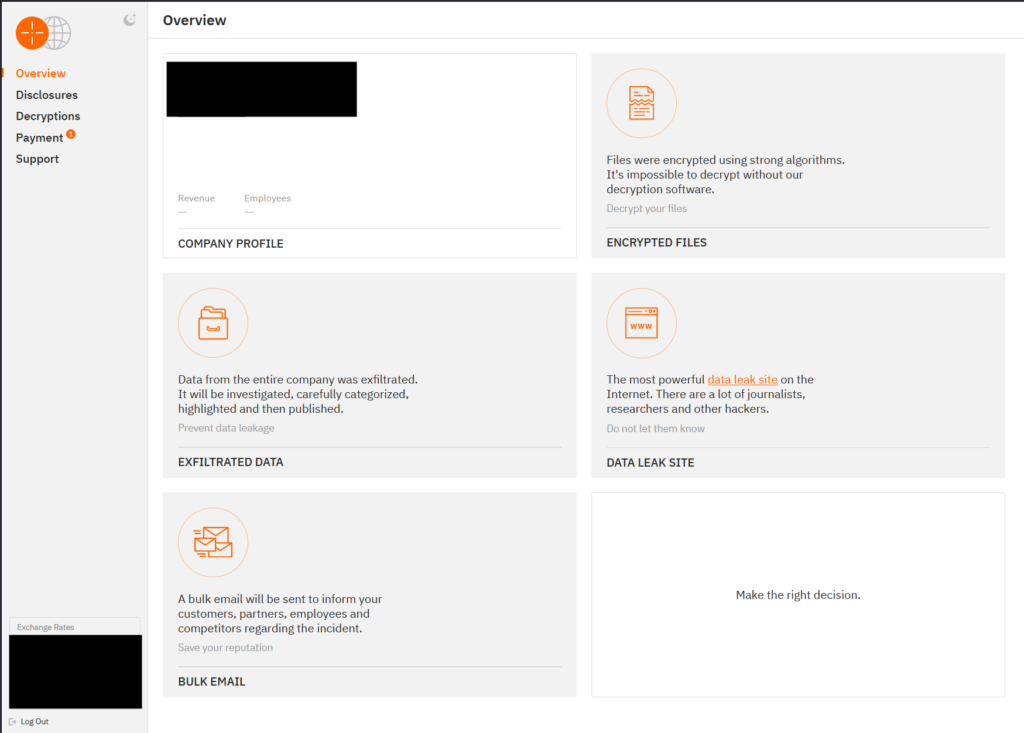
The “Disclosures” section of the victim portal allows victims to retrieve a list of data that the group claims to have exfiltrated, and the “Decryptions” section allows users to upload five encrypted files to confirm the group’s ability to decrypt files. As ransomware negotiators commonly request a list of exfiltrated files to establish proof of data theft, this process may serve to speed the negotiation process and increase the group’s credibility in the eyes of the victim.
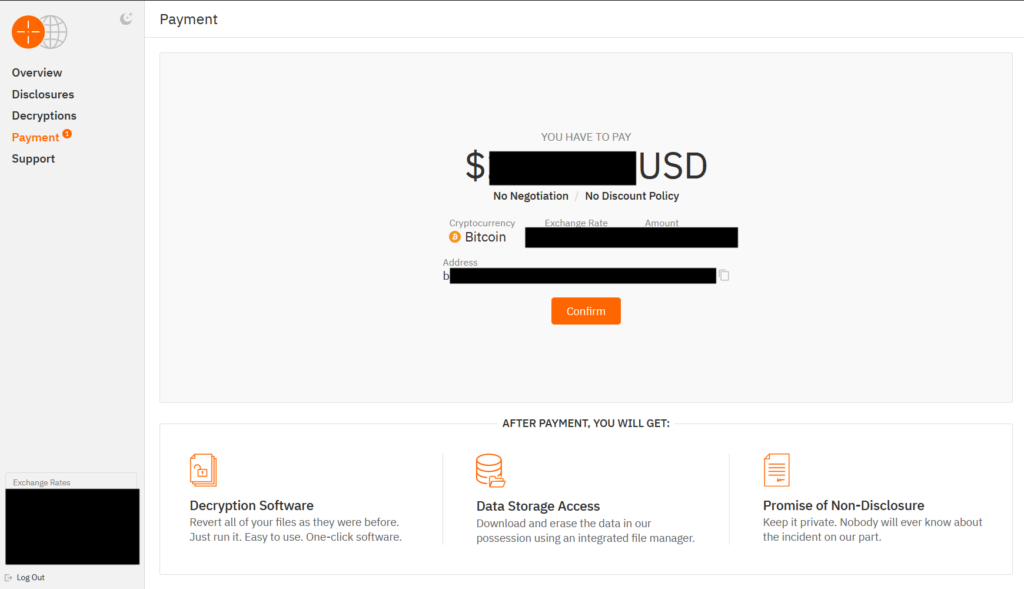
The “Payment” section contains the ransom demand pre-determined by the threat actor; we do not know whether this amount is set by the core group or the individual affiliate, nor the basis on which the amount is determined. The page provides the desired cryptocurrency type and a wallet address up-front, as well as current exchange rates, likely also intending to streamline the settlement or negotiation process. Interestingly, the section contains the note “No Negotiation/ No Discount Policy,” implying that the group refuses to offer discounts or otherwise negotiate the ransom payment. GRIT’s interactions with Hunters International have shown this to not be the case, and the group is confirmed to have accepted lower ransom payment amounts following negotiations.
The final section of the victim portal, “Support”, contains a chat interface where the victim can send messages directly to the threat actor, as seen in many other ransomware victim portals; we do not know if negotiations are handled by the “core” group or individual affiliates. The placement of the support/ chat functions on a streamlined page alongside all other relevant logistical details associated with ransomware communications suggests an intentional investment into the portal, providing the group with a credible image and reducing opportunities for user error, an advantage over smaller or less-resourced ransomware groups. Hunters International’s upfront handling of common ransomware negotiation questions – such as ransom amount, and exfiltrated data – indicates likely familiarity with ransomware negotiations and a desire to prevent opportunities for “stalling” by victims, both of which suggest experienced operators.
Hunters International’s increased operational tempo over the past quarter suggest that the group may be “hitting its stride”, attracting new affiliates, or both. GRIT assesses that the group intends to continue operations in the mid-to-long term, and will most likely continue to increase its victim volume in the near term. While we have not directly observed Hunters International performing “triple extortion” operations or escalated coercive tactics, these may be implemented as the group becomes better resourced and more mature.
Other Notable Ransomware Events
Operation Endgame
On May 30th, 2024, international Law Enforcement Organizations from the United States, Denmark, France, Germany, the Netherlands, and the United Kingdom announced the disruption of IcedID, Smokeloader, Pikabot, Trickbot, and Bumblebee botnets, dubbed “Operation Endgame.” The disruption efforts resulted in the arrests of four individuals linked to the botnet operations, and the search of 16 premises likely used by the threat actors for their operations.
The Law Enforcement agencies behind Operation Endgame have maintained a dedicated website to showcase the results of the operation, emulating a precedent set by Operations Cronos’ disruption of LockBit. The website includes links to a Telegram channel and email point of contact, encouraging visitors to “reach out,” as well as video productions with cryptic expressions such as “Did you think we weren’t on to you?” before displaying a website seizure notice. These kinds of taunting messages appear to have become more frequent in law enforcement messaging as part of large-scale disruption operations and may be intended to sow discord or distress among affiliated cybercriminals.
At the time of this report, additional developments advertised on the Operation Endgame website include a video explaining that Law Enforcement agencies are currently targeting the user behind the moniker “Odd,” and are looking for information that will lead to the arrest of the individual behind the moniker.
The disruption of these botnet operations will likely have a moderate impact on ransomware operations in the short term, as many initial access brokers rely on botnet services to gain initial access to victim environments. However, as a relative comparison, a similar disruption of the Emotet botnet was announced in January 2021, but its effects proved to be short-lived. Just ten months later, the botnet’s operators were able to restore capabilities and begin rebuilding their network of victim machines. We assess that operators of the IcedID, Smokeloader, Pikabot, Trickbot, and Bumblebee botnets will attempt to follow suit, and similarly attempt to bring their botnets back to life over the course of the next year.
LockBit Developments

Source: Analyst1
In February 2024, a multinational law enforcement operation led by the UK National Crime Agency (NCA) seized the infrastructure of the prolific Ransomware-as-a-Service (RaaS) group, LockBit, following alleged “infiltration” of the group and takeover of LockBit’s services. LockBit’s administrator, under the long-term persona “LockBitSupp,” subsequently rebuilt or recovered additional infrastructure, claiming to have been unimpeded by any disruption within a month. As rumors circulated as to the known identity and possible law enforcement cooperation of LockBitSupp, the group also posted a decreasing volume of victims on their DLS in April, suggesting that Operation Cronos may have been more disruptive to LockBit’s operations than was immediately clear.
In early May, Operation Cronos appeared to return with a vengeance, using previously seized infrastructure to tease additional public disclosures before announcing LockBitSupp’s true identity on May 7th, 2024 – concurrent with the announcement of sanctions by the US, UK, and Australian governments. LockBitSupp has been identified as Dmitry Yuryevich Khoroshev (Дмитрий Юрьевич Хорошев), “a Russian national and a leader of the Russia-based LockBit group.”
As news broke of this unmasking, the LockBitSupp persona’s account proclaimed that the attribution was false and that Khoroshev was not affiliated with LockBit, in a series of posts on illicit forums and in interviews.
Amidst the sanction announcements, Operation Cronos also released additional information about LockBit’s operations, including the following:
- Up to 114 LockBit affiliates never received any ransom payments from their operations
- Following a high-profile attack against a children’s hospital in December 2022, LockBitSupp publicly declared that the attacking affiliate had broken the group’s rules and was no longer associated with the group. This statement was a lie, as the affiliate continued operations in at least 127 unique attacks afterward.
- LockBit did not routinely delete stolen data following ransom payment receipt, despite claiming to the contrary and providing ostensible proof of having done so.
Following the initial February 2024 operational disruption by Operation Cronos, LockBit resumed bosting alleged “new” victims, some of which appeared to be duplicates of historical victims and others which appeared to be recent victims that had not yet been posted. Since Khoroshev’s unmasking, the LockBit data leak site has similarly seen a surge in victim posts, particularly given the noticeable decrease in April. We do not know to what extent this surge of victim posts represents truly new victims rather than recent victims being posted with greater urgency, though we assess that LockBit’s administrators have been and continue to focus on projecting an image of a secure, continuing RaaS operation, likely to avoid further “spooking” the group’s remaining affiliates.

At the time of this report’s writing, LockBit’s second-generation infrastructure remains up and running, and the group continues to post new victims to its data leak site. We anticipate that Khoroshev’s identification and subsequent sanctions will almost certainly reduce the revenue potential associated with LockBit ransomware operations against western targets, as western victims now face legal consequences to ransom payment. We assess with moderate confidence that the continued law enforcement disruption of LockBit will lead at least some affiliates to abandon the group and make LockBit a less appealing destination for affiliates in the future. While LockBit continues to post victims at this time, we expect victim volume to gradually decrease as any remaining “backlog” is posted, assuming that fewer affiliates will result in fewer victims.
Regardless of the skill and tenacity of LockBitSupp, Khoroshev, or any other members of the LockBit group, it is hard to imagine times getting any easier for LockBit in the near term. We will continue to monitor the victims claimed by LockBit in the future, as well as for signs in open and closed channels that may reflect a substantial flight of affiliates. We remain optimistic that in the long term, Operation Cronos will serve as an early model for the successful disruption, influence, and eventual dismantling of modern RaaS operations.
Sources:
- U.S. Department of the Treasury | United States Sanctions Senior Leader of the LockBit Ransomware Group | May 7th, 2024
- U.S. Department of Justice | U.S. Charges Russian National with Developing and Operating Lockbit Ransomware | May 7th, 2024
- UK National Crime Agency | LockBit leader unmasked and sanctioned | May 7th, 2024
- United States District Court, District of New Jersey | United States of America v. Dmitry Yuryevich Khoroshev | May 2nd, 2024
- Analyst1 | Ransomware Diaries Volume 5: Unmasking LockBit | May 7th, 2024
Notable Newcomers
GRIT began tracking four new ransomware groups in the month of May. This group of newcomers distinguishes themselves from previous months’ with their relatively “quick starts.” All four of the newly observed groups, which include DAn0n, Spacebears, Underground, and Arcusmedia, posted at least nine alleged victims in May, placing them roughly in the “middle of the pack” amongst competitors by victim volume, and even exceeding the operational tempo of Established groups such as Medusa and Rhysida.
New ransomware groups are seldom this quick to increase operations tempo “out of the gate.” As we have assessed in our Taxonomy and Ransomware Lifecycle white paper, altogether “new” groups – that is, groups that have not rebranded or splintered from other operating ransomware groups – tend to start their operations slowly, most often claiming only a handful of victims in their first month. These Emerging groups may increase their victim counts over shorter periods of time should they continue to mature and increase their operational efficacy over time, eventually placing them within the category of a longer-term “Developing” group.
Mays newcomers have bucked that trend, at least insofar as it is evaluated by victim volume. There are a number of possible explanations for these anomalies, ranging from the groups having operated for some time without a data leak site, to increased affiliate “flight” post-disruption of Alphv and LockBit. In the former case, we observed similar behavior from 8Base and Akira, both of whom appeared with a substantial number of victims claimed all at once at the data leak site’s onset, and which we assessed reflected operations preceding the data leak site’s launch.
In the latter case, operational disruptions of Alphv and LockBit has led to at least some affiliate departures, and we have assessed in previous GRIT Ransomware Reports that some displaced affiliates may land amid “newer” Raas Groups, such as RansomHub or Medusa. This assessment has borne out, at least in part, with reports of former Alphv affiliates having joined RansomHub since Alphv’s disbanding. For other “newer” ransomware groups, better profit-sharing splits, internal resources, and management eager to attract experienced operators may make even unheard-of RaaS groups attractive in the near-to-mid-term, or may encourage other experienced operators to “strike out on their own”–forming new groups in the process.
Overall, determining the exact landing spot of every displaced affiliate is unlikely to be a surmountable task, though limited tracking and anecdotal outcomes may be identified by open-source collection and identification of overlapping behavior or infrastructure. The possible scenarios outlined above could all plausibly contribute to higher-than-normal victim volume at the outset for these new groups, as could historical operations preceding the launch of a data leak site. Continued performance at levels above baseline for Emerging groups in the coming months will be a telltale indicator as to whether the groups’ higher operational tempos are the result of experienced operators or groups that have operated for longer than their data leak sites may indicate.
Ransomware Forecast: Moonstone Sleet
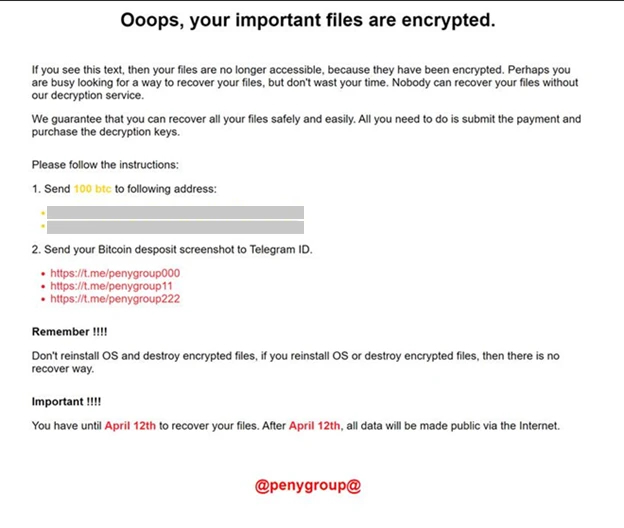
In late May 2024, Microsoft released a blog detailing the emergence of a new North Korean threat actor, Moonstone Sleet, responsible for a range of malicious activity including ransomware. Microsoft has observed the delivery of a custom ransomware variant, dubbed “FakePenny,” by the group as far back as April 2024, using a ransom note that closely mirrors that of Russian APT Seashell Blizzard (also known as Voodoo Bear, Sandworm, or APT44) in the 2017 NotPetya attacks.
Microsoft notes that with an observed ransom demand of $6.6M USD in BTC, the group’s ransom was markedly increased relative to historical North Korean ransomware groups, such as the self-proclaimed “H0lyGh0st” (tracked by Microsoft as DEV-0530), which have impacted small-to-midsized businesses. As with many North Korean cyber operations, the most likely goal of Moonstone Sleet is financial gain as a means to support the DPRK regime and national objectives.
North Korean threat actors have performed ransomware operations in the past, including those performed by DEV-0530, the DPRK’s reported 2022 use of the Maui Ransomware to target healthcare and the public health sector, and 2017’s worldwide WannaCry ransomware attack at the hands of the Lazarus Group. But ransomware appears to account for a minority of publicly disclosed North Korean cyber operations, with concurrent operations focused on cryptocurrency theft or attacks on critical infrastructure and financial institutions observed more frequently.
Ransomware operations attributed to North Korean actors typically follow similar processes as those seen deployed from Eastern Europe, with the use of encryption, a dedicated .onion dark web site, and payment demands in cryptocurrency. Were North Korean threat actors to obtain substantial revenue from successful ransomware operations, we assess with low confidence that their frequency and global spread will increase. However, due to increasing security resilience to ransomware in the western world, such success is far from given. In the meantime, continued application of best practices–including the use of Endpoint Detection and Response, network segmentation, enforced Multifactor Authentication (MFA), and attack surface minimization efforts–will likely serve to make modern organizations a harder target.
Source: Microsoft Threat Intelligence
Sources:
- Microsoft Threat Intelligence | Moonstone Sleet emerges as new North Korean threat actor with new bag of tricks | May 28th, 2024
- Microsoft Threat Intelligence | North Korean threat actor targets small and midsize businesses with H0lyGh0st ransomware | July 14th, 2022
- Cybersecurity and Infrastructure Security Agency | #StopRansomware: Ransomware Attacks on Critical Infrastructure Fund DPRK Malicious Cyber Activities | February 9th, 2023
- Cybersecurity and Infrastructure Security Agency | North Korean State-Sponsored Cyber Actors Use Maui Ransomware to Target the Healthcare and Public Health Sector | July 7th, 2022
Final Thoughts
On its face, May 2024 brought the highest volume of ransomware victims observed since the start of 2024, though the true extent of ransomware’s impact over the period is difficult to ascertain with LockBit’s “dump” of victims substantially skewing the dataset. In the coming months, we expect LockBit’s performance to reveal whether their May 2024 performance stood as a ”show of force” or more of a “death rattle.” Regardless, with the bravado of LockBitSupp on full display in recent months, the likelihood of the group abruptly ceasing operations is low, and we would instead expect to see continued reduction in operational efficacy.
In line with our assessments from recent Ransomware Reports, one ransomware group’s loss is another’s gain. Newer groups such as RansomHub are almost certainly benefiting from the experience of former Alphv affiliates, and present or former LockBit affiliates will likely seek similar outlets to continue their operations with less perceived law enforcement pressure. We expect to see continued efforts by other ransomware groups to attract current and former Alphv or LockBit affiliates, including through more affiliate-friendly practices – such as RansomHub’s policy of payment directly to affiliates before profit-sharing with the core group. We may also see closed or open commentary or “testimonials” from affiliates that have successfully “jumped ship” as part of these narratives.
Similarly, some displaced affiliates may opt to “strike out on their own”, leading to newly identified groups and an increase of distinct ransomware groups operating at any given time. It remains to be seen whether this has already occurred and whether such groups will operate for the long term, consolidate to benefit from economies of scale, or “flame out” early on. We are monitoring this possible “dispersion” of ransomware operators across a larger number of groups with concern and expect that a greater number of smaller groups would complicate attribution and law enforcement prosecution.
In 2023, we observed similar levels of activity between May and June, but with expected decreases in LockBit operational activity in the near term, we assess that some level of decreased victim volume is more likely than stagnation or increase in June 2024. This decrease in overall momentum and observable victim impacts speaks to the importance and success of international law enforcement operations that impact not only the means but also the will of the adversary. Continuous efforts to impose consequences (affiliate arrests and identification) and minimize rewards (enforcing sanctions that prevent payment) are likely critical to keeping pressure and ransomware groups going forward. We look forward to observing and reporting on the long-term effects of these efforts and others in the future.
The GRIT Ransomware Taxonomy
By subdividing ransomware groups, GRIT can obtain more detailed insights into how ransomware groups progress in their level of operational maturity and can classify and identify potential rebranding activity.
We distinguish ransomware groups by placing them into these six categories:
EMERGING
This category is reserved for new ransomware groups within their first three months of operations. These organizations may be short-lived, resulting in an Ephemeral group; may be determined to have Splintered or Rebranded from an Established group; or may move on to further develop their operations and TTPs over time.
EPHEMERAL
These groups are short-lived, with varied but low victim rates. Observed victims are usually posted in a single or short series of large postings rather than a continuous flow over time. Ephemeral groups, by definition, terminate operations, spin-off, or rebrand within three months of formation. These groups may or may not have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
DEVELOPING
These groups have conducted operations for three months or longer, resulting in a recurring flow of victims. Developing groups do not appear to be directly linked to other ransomware groups as a Splinter or Rebrand but may include some experienced ransomware operators. Developing groups generally improve their people, processes, or technology over time by recruiting additional members, refining TTPs, or improving the quality of their associated ransomware and encryption. These groups generally have dedicated infrastructure (i.e., data leak sites and chat support) as part of their operations.
SPLINTER
These groups consist of a plurality of members from previously Developing or Established groups and may have formed either by choice or due to exclusion. These groups may be identified by very similar or overlapping TTPs and tooling or through HUMINT gathered through interactions with personas on the deep and dark web. Splinter groups differ from Rebrands by the continued existence of the original organization as the Splinter group operates.
REBRAND
These groups consist in whole, or in part, of former Developing or Established groups. Rebrands often maintain the same people, processes, and technology as the original group. Rebrands are generally undertaken in order to minimize attention from law enforcement or intelligence officials or to avoid negative publicity.
ESTABLISHED
These groups have operated successfully for at least nine months and have well-defined and consistent tactics, techniques, and procedures. Established groups often possess functional business units that enable sustained ransomware operations, with specialists focused on areas such as personnel, encryption, negotiations, etc. These organizations successfully employ technology and redundant infrastructure to support their operations.
There are multiple routes a group can take through the various classifications, and no one route is standard. While one group may begin as “Ephemeral” and move their way through the ranks to “Full-time,” another group may enter as a “Rebrand” as part of a larger obfuscation strategy to avoid attention from law enforcement.