
GRIT Ransomware Report: November 2022
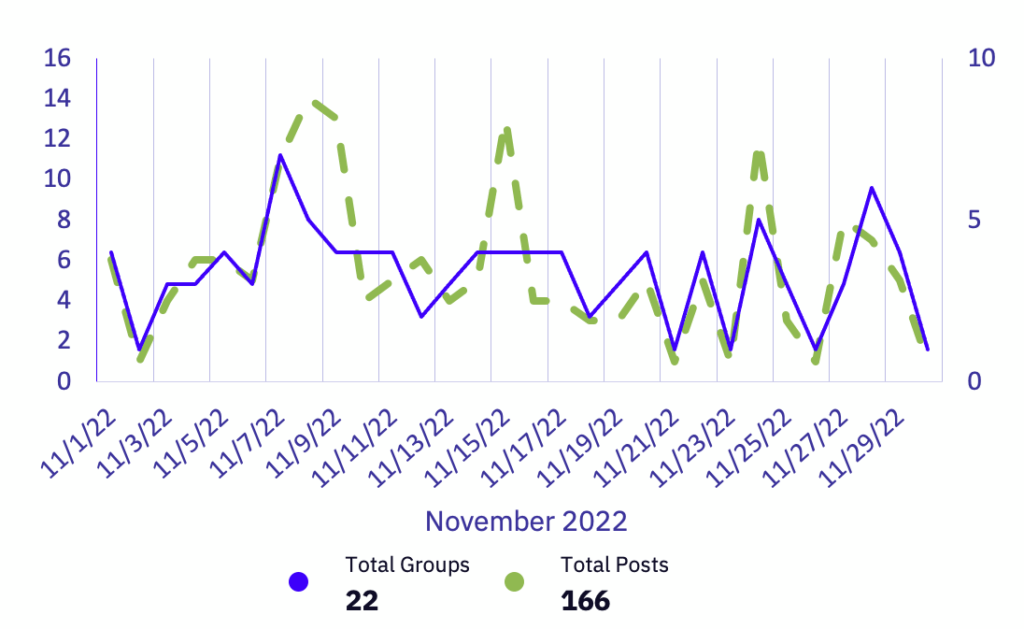
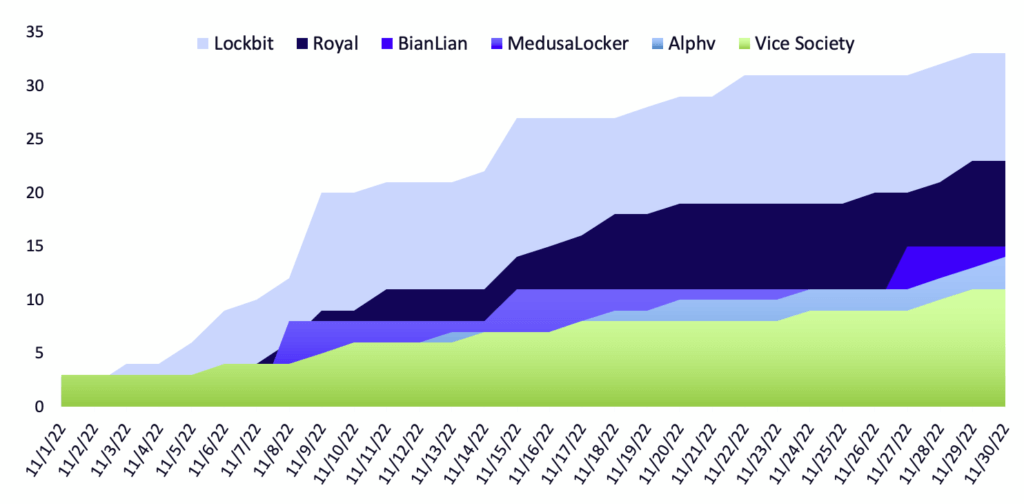
In November, GRIT observed 22 active groups accounting for 166 victims. Continuing their trend from previous months, Lockbit’s claimed victims fell by a massive margin, dropping 41% from their October haul. November represents Lockbit’s slowest month this year, falling even lower than they did during their June to July lull when switching from Lockbit2 to Lockbit3. Lockbit wasn’t alone in their slowdown, as eight other groups also saw at least a 40% decrease in reported victims.
GRIT began tracking four additional groups this month, including Royal and MedusaLocker, who immediately jumped into the top five groups based on total reported victims. These four groups accounted for 43 reported victims in November. An additional six groups with no activity in October showed a minor resurgence, accounting for 26 victims in November.
In addition to having less reported victims, November also saw less countries and industries targeted. Specifically, 33 industries were impacted this month compared to 36 in October. Similarly, 38 countries were impacted in November compared to 40 countries in October. These slight decreases suggest that there were no significant changes to targeting this month. While there were some shifts in the order of the most targeted industries, the most noteworthy changes included the Legal industry shifting into the top 10, knocking Government organizations off the list, and the Construction industry dropping from third place to tenth. In terms of countries targeted, GRIT noted that India and UAE were among the top ten victimized nations, pushing Spain and Australia out of the top ten.
GRIT’s data in this report includes updated insights into threat actor activity from October obtained from recently published leak sites that included historically compromised victims. The addition of this dataset had slight impacts to victim trends and statistics from previous months; however, it did not have significant impacts on trends or findings from previous reports.
Ransomware Trends
Based on sources monitored by GRIT, there was a 12.6% decrease in the total number of victims from October to November. However, the number of active groups increased from 17 to 22 during this time, including four groups that we began tracking this month: MedusaLocker, Project Relic, Royal, and Mallox (also known as FARGO). Nine of the groups that were active in October–Alphv, BlackBasta, Everest, Ransomhouse, Ragnarlocker, Blackbyte, Quantum, Snatch, and Lockbit–each saw a decrease in victims of more than 40%. Additionally, six groups that were inactive in October were responsible for 26 victims, while the four newly tracked groups were responsible for 43 victims.
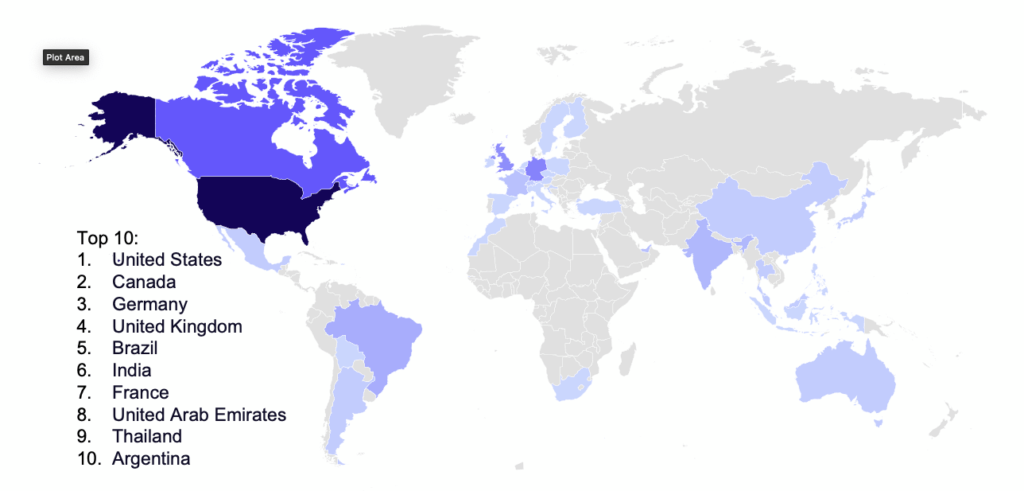
The top ten countries targeted in November were the United States, Canada, Germany, United Kingdom, Brazil, India, France, United Arab Emirates, Thailand, and Argentina. There was a significant decrease in the targeting of Spain, Australia, and France, with Spain experiencing the largest decrease at 85.7%. On the other hand, Canada and the UAE saw significant increases in targeting, with Canada experiencing an increase of 160%. There were minor decreases in victims from Italy, Japan, Philippines, Brazil, and Thailand. In total, 38 countries were targeted.
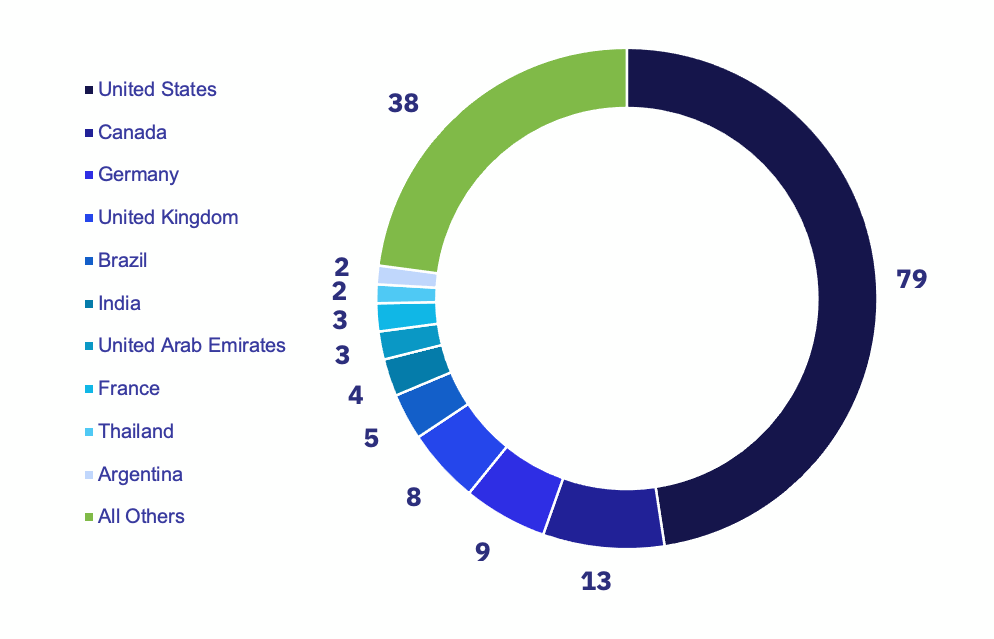
In October, we observed that Lockbit’s competitors were quickly catching up, and now Lockbit has dropped to just 20% of all reports, a mere 10 ahead of Royal–a group that we only recently began formally tracking. The USA still represented 47.6% of targeted victims. The top 8 countries by the distinct number of industries targeted were the US, Canada, Germany, the UK, Brazil, India, the United Arab Emirates, and France.
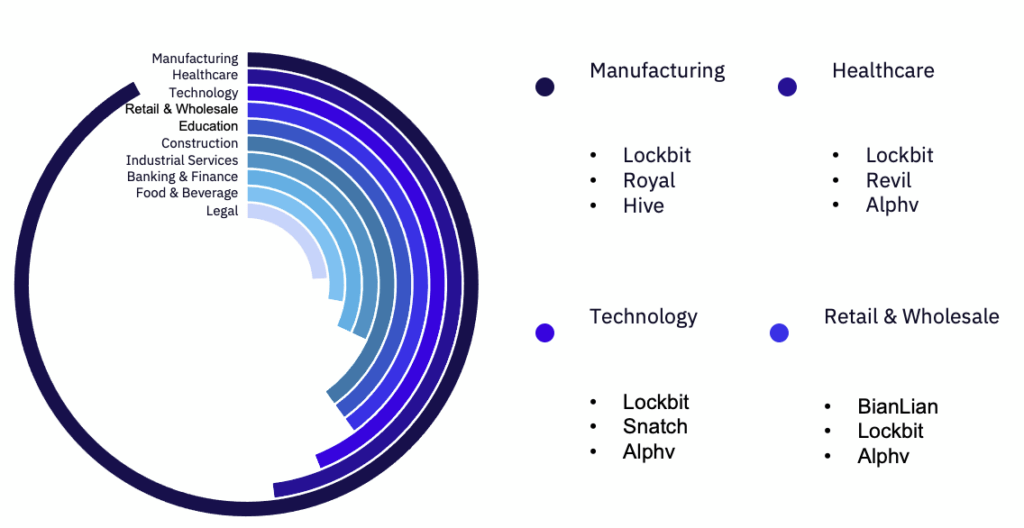
Among the top targeted industries, the most active groups were Lockbit, Royal, and Snatch. There were significant increases in victims in the Consulting and Electronics industries, while the biggest decreases in victims were seen in the Construction, Media and Advertising, Telecommunications, and Healthcare industries. GRIT observed targeting against 33 of the 40 tracked industries in November. By far the most targeted was the Manufacturing industry, where the most targeted countries were the US, Canada, and Taiwan.
In November, Lockbit maintained its position as the most active group, but its overall share of victims decreased from 29% to 20%. Royal is a relatively new group that has seen a spike in activity, posting an average of one victim every two days. BianLian also increased its standing from 4th place to 3rd place, despite only posting one more victim in November than was observed in October.

Threat Actor Spotlight – MedusaLocker
MedusaLocker is a ransomware group that was first observed in late 2019, and CISA released an alert about the group in June 2022 (revised in August 2022). Available reporting indicates the group favors using vulnerable RDP configurations, phishing emails with attached ransomware executables, batch files to execute PowerShell scripts, and it has been known to spread through registry modifications and host/network/shared storage detection. In November 2022, the group had 11 publicly disclosed victims with no clear focus on a specific industry, however, nearly half of these victims were based in the US. MedusaLocker’s ransom notes claim to leak the data of victims who do not pay the ransom, an increasingly common tactic to exert more pressure on victims. As of late November 2022, the group’s leak site was down, but its chat infrastructure appeared to still be functional.
Other New and Notable Ransomware Events
New Leak sites: In November, we noticed a new leak site for Mallox ransomware, also known as FARGO. Mallox seems to be a rebrand of the TargetCompany ransomware group and started operating in mid-2021.
New group: We also came across a new group called ProjectRelic. We are currently developing intelligence and creating a threat profile for this group; however, we do know that their encryptor is written in Go, and they talk to their victims through a custom Tor chat app.

Notable: A leak site attributed to revil claimed three victims in November. In total, revil has claimed 11 victims this year, with bursts of activity starting in May 2022.
Final Thoughts
GRIT observed an interesting trend of October’s top three ransomware groups, Lockbit, BlackBasta, and Alphv, which accounted for 1/3 of the total decrease in ransomware victims from November. In fact, these three groups saw a combined 54 fewer victims than was observed in October, amounting to a combined decrease of 50.5%. The decrease in reported victims is noteworthy, but understanding the cause of this decrease over several months is more difficult. While there is no definitive evidence supporting the causes behind these decreases, it may be the case that ransomware groups and affiliates are targeting organizations who are more incentivized to pay ransoms before the ransomware groups post their information on leak sites, as well as those more heavily impacted if kept offline during the holiday season, as noted by CISA in Alert AA21-243A.
Geographically, GRIT observed the biggest increase in victims operating in Canada, shifting from four victims in October to 13 in November. This observation contrasts with a steep decrease in victims in Spain, where the victim count decreased from seven to one over the same timeframe. Among other countries, GRIT saw consistent, yet small, deviations in the number of victims from the month prior. Additionally, we observed 15 countries targeted in October but not at all in November.