October demonstrated an interesting month in the ransomware environment. Lockbit, the most prolific ransomware group in 2022, saw a massive 49% decrease in reported victims. Hive had a similar trend, with a decline from 14 victim posts in September to only two in October (an 85% decrease). Nine groups active in September posted no new victims in October.
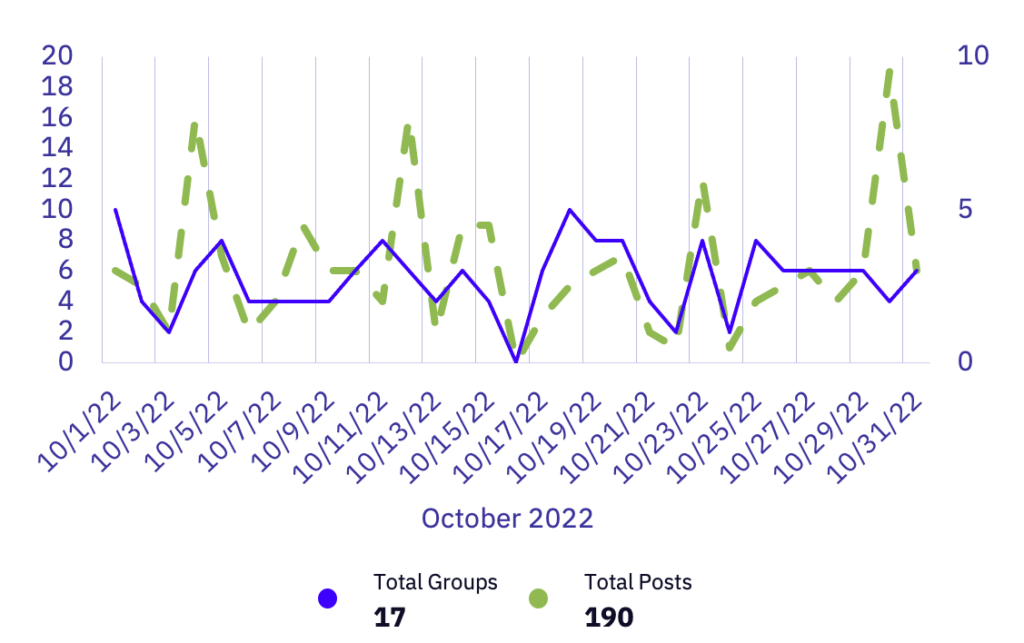
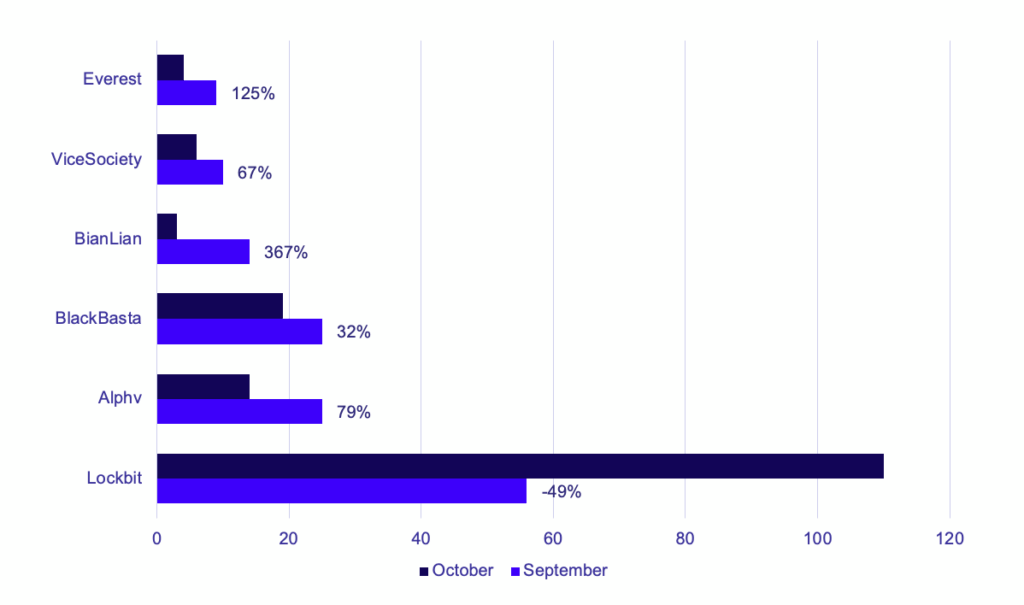
While Lockbit and Hive saw significant decreases in victims, eight groups published increases of five or more victims in October compared to their claimed number of victims in September. Among these eight groups there was an increase of 62 more victims than they had the previous month, highlighting their increases in operations.
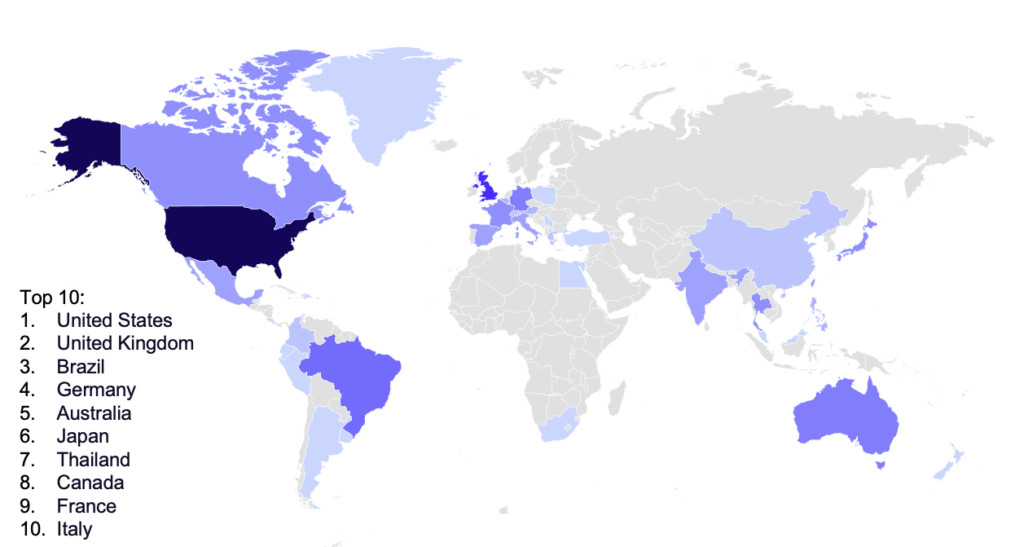
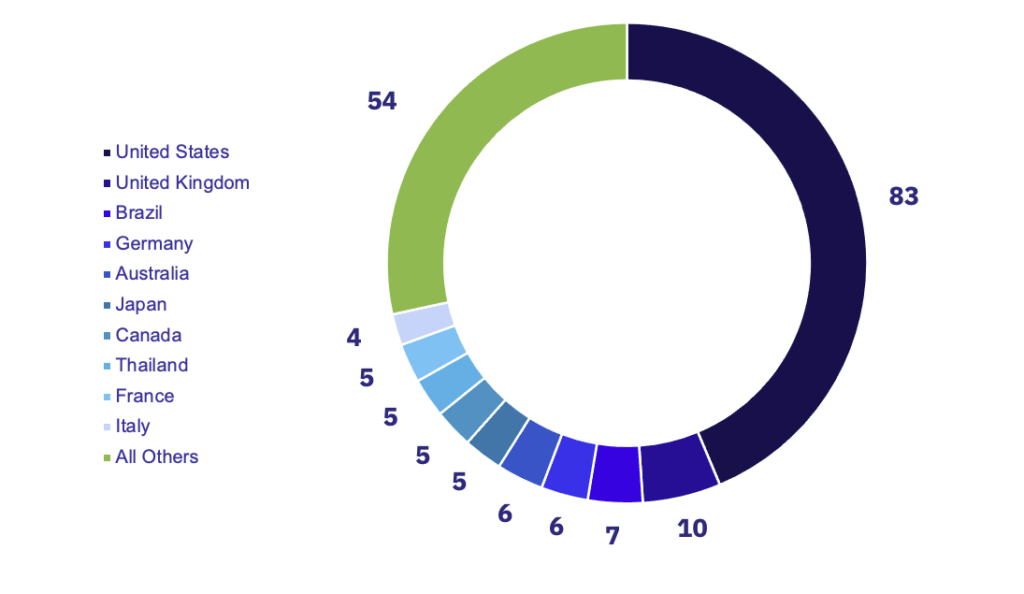
Spain and France saw the largest decrease in posted victims, due to a lack of new activity from Sparta and a significant decrease in activity from Lockbit, both of which targeted these countries disproportionately in September. The United States remains the most victimized country, seeing a 7.8% increase from September to 83 victims, 73 more than the second most targeted country, the United Kingdom.
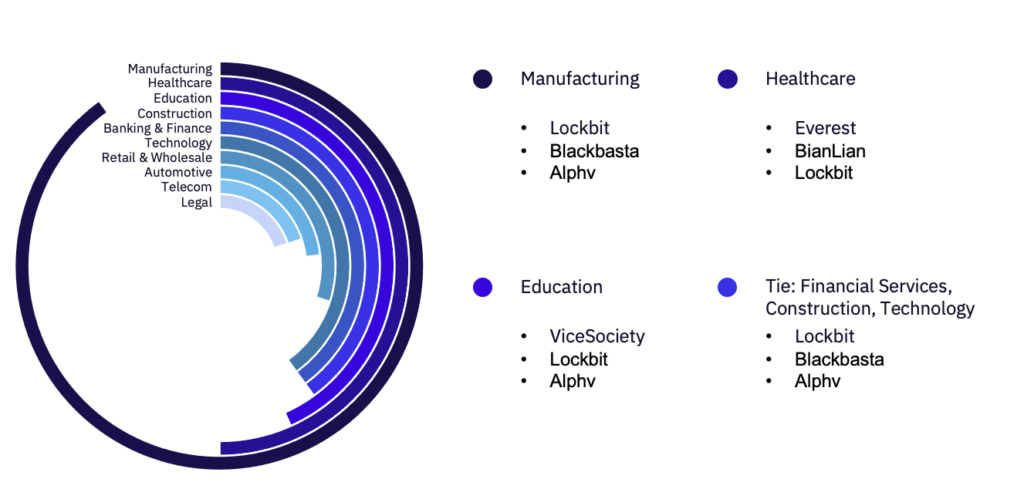
Among the previous month’s top five impacted industries, manufacturing saw an increase of seven reported victims and continues to be the most impacted industry vertical in 2022, and Healthcare saw an increase of one. The remaining three industries, Technology, Construction, and Government, all saw at least a 20% decrease in reported victims compared to the previous month.
These changes do not demonstrate any clear trends yet but may lead to new observations across the ransomware landscape. GRIT will continue to monitor for new changes which may help develop a better understanding of ransomware actors and affiliates behavior.
Ransomware Trends
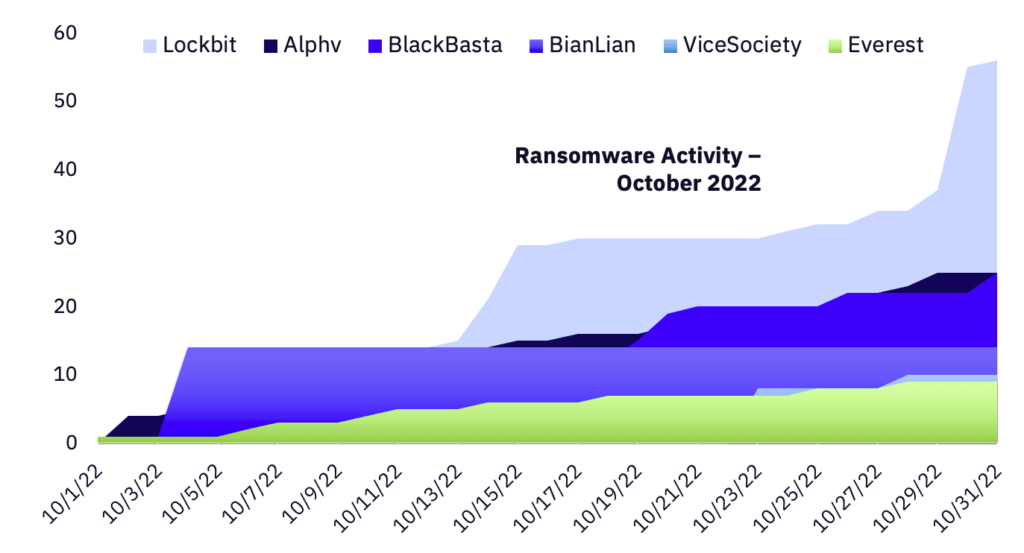
Alongside a 7.32% decrease in publicly posted ransomware victims, October also saw a decrease in actively tracked ransomware groups–from 20 in September down to 17. As a more specific touchpoint, Lockbit’s average victims per day in Q3 was 2.5, with a single-day peak of 35. In October, that average dropped to just 1.9 victims per day, with a one-day peak of 18. In fact, Lockbit had an 11-day streak of 1 or fewer reported victims, which is unusual given their usually-prolific activity. Hive, another prolific group, also saw a steep drop in reports, plummeting from 14 victims in September to just 2 in October. However, making up for the decrease in Lockbit and Hive’s activity, 14 groups showed large increases in reported victims.
Geographically, the most significant decreases were seen in France and Spain, which were down 78% and 74% respectively. The decrease in Spain is likely due to the lack of activity from Sparta, a group we highlighted in the Q3 Ransomware Report published last month. France’s decrease appears to be mostly attributable to a large spike in French victims posted by Lockbit on September 14th followed by Lockbit’s rapid decline in activity through October.
The most surprising aspect of October has certainly been the dearth of activity from Lockbit. For the first time since GRIT began actively tracking and reporting on monthly ransomware trends, Lockbit has been overtaken by another group for targeting against the US. Blackbasta took the lead for the month with 21 US victims, followed by Lockbit and then Alphv with 14 and 12 victims respectively.
Of the 40 industries tracked by GRIT, 36 were observed to have victims in October. With 25 victim industries this month, the USA still firmly holds the top spot for industries targeted, followed by the UK in second place with eight industries. The USA still represented the dominant share of targeted victims, despite the decline in attacks from groups like Lockbit and Hive which usually make up the majority of USA-based attacks.
Continuing previous trends, the Manufacturing and Healthcare industries saw the most active targeting, with Education coming in third place and Financial Services, Construction, and Technology industries tying for fourth. Among these top industries, the most active groups were Lockbit (even with their dramatic downturn in activity), Blackbasta, and BianLian. For manufacturing specifically, victims were predominantly based in the USA, China, and Italy. The largest increases in victim targeting were seen among Manufacturing; Telecom; Media and Advertising; Pharmaceutical; and Aerospace, Defense, and Military industries.
Drilling down into individual group activity, Lockbit is still the most prolific group based on their number of reported victims, even after their rapid decline in activity for the month. While numbers were down overall, Lockbit’s hold on the title of “most active group” highlights just how prolific they were in previous months, despite the severity of their decline in activity. However, because of their drop-off in reported victims, their overall share of victims also fell from 54% in September (with 110 victims reported) to just 29% in October (56 victims).
In contrast, AlphV pressed hard in October and nearly doubled their victim postings. On average they maintained a pace of almost one victim post per day, with 25 this month compared to 14 last month.
Tying AlphV for victim posts, Blackbasta had their most active month since their inception.
Threat Actor Spotlight – Everest Ransomware Group
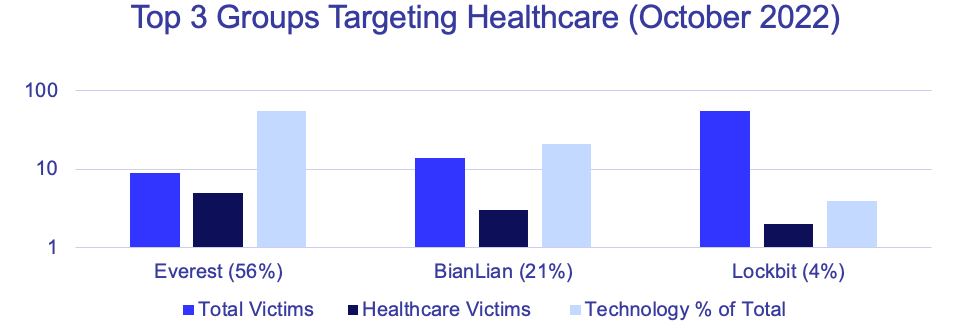
With only one exception, Everest seems to prefers to be “low and slow” and has only ever posted one victim per day in 2022, however GRIT observed an increase in frequency starting in mid-September. The group has had a significant focus on South American government entities through 2022, but their list of 47 publicly disclosed victims also includes targeting AT&T in October, as well as the New York State DMV.
Top industries targeted by Everest include Healthcare, Government, Legal, and Manufacturing. In October they were the top group targeting the Healthcare industry. So far in 2022 they have predominantly focused on targets in the US and Canada.
Other New and Notable Ransomware Events
In the course of gathering data for this month’s report, we observed that leak sites associated with the Sparta and Cheers ransomware groups were no longer browsable. At this point, it is unclear whether they are down for good, or have just gone temporarily offline.
Sparta made waves last month with their rapid-fire Spain-based targeting and publishing of 14 victims in the middle of the month before going radio silent.
On the other hand, the Cheers ransomware group has shown very little activity since their inception in late May of this year. After publishing four victims in their first month, they’ve released no more than three victims per month since. We first observed their leak site was down in mid-September, and haven’t seen any activity from the group since.
Additionally, two new groups–Qilin and Shaoleaks–were observed. Qilin, also reported as “Agenda”, published a leak site on October 8th with six victims, across six industries, in six different countries. While there appears to be no apparent relation among the victims, the serendipity of these numbers being posted in the month of Halloween is at least amusing.
Shaoleaks emerged just in time to sneak under the wire for the October report, with just four posts including two victims on October 31. The group then went offline the following day, but GRIT is continuing to monitor the group’s operations.
Final Thoughts
While two of the biggest ransomware actors saw a combined 53% decrease in reported victims, the total victims published across GRIT’s dataset only decreased by 7.3%, indicating a major increase among the remaining ransomware organizations. If this shift continues, we may see a major increase in targeting from groups toward organizations impacting potential loss of life, such as Healthcare, Utilities, and Energy.
The continual increase in US-based victims indicates that these threat groups still perceive US-based organizations to be the most lucrative targets. 21 other countries saw an increase of three or fewer victims compared to September, while only seven countries saw a decrease in victims from the month prior. This indicates threat groups are continuing to expand their targeting across the globe.
Lastly, some industries are seeing targeting they previously hadn’t in September, with the Chemical and Pharmaceutical industries seeing two and three publicly disclosed victims, respectively. Targeting against the Pharmaceutical industry, especially going into Flu season, may increase if it’s observed to negatively impact their ability to produce life-saving materials. Decreases of 80% or more occurred in a number of luxury industries, including Entertainment, Hospitality, and Travel.
Nic Finn
Senior Threat Intelligence Consultant,
GuidePoint Security
Nic Finn is a Senior Threat Intelligence Consultant on GuidePoint Security’s consulting team, where he engages in threat intelligence development and reporting on behalf of the firm’s clients. His career background includes cybersecurity operations for several clients over various verticals.
Nic joined the GuidePoint team from Sophos’ Managed Threat Response (MTR), where he was a Team Lead directing operations for a 10-member team. Prior to MTR, Nic served the United States Air Force (USAF) as a Special Agent in the Office of Special Investigation (OSI), a Military Criminal Investigation and Counterintelligence organization. Within OSI, Nic served roles in felony-level and fraud investigations and as a Cyber Investigations and Operations Case Agent.
In addition to various roles in cybersecurity and counterintelligence, Nic served as a Weapons Director, controlling USAF combat aircraft during training and live-fire air-to-air engagements and exercises.
Nic has excelled in numerous forensics and cyber security courses, obtaining various certifications in digital evidence collection, cyber investigations, and forensic analysis.
