Part 2: The Three Lines of Defense are a’changing
Posted by: Brian Betterton

In part 1, we mentioned that the Institute of Internal Auditors (IIA) had recently opened up a request for public comments on its proposed changes to their Three Lines of Defense (3LOD) risk management and control model. They have just released a summary of those public comments. Now we will pick up from there to discuss a little more background on this model.
In 2013, The Institute of Internal Auditors (IIA) released their position paper called “The Three Lines of Defense in Effective Risk Management and Control”, to help clarify the 3LOD model that had been around for years prior to then. That 2013 paper said (and included the diagram following):
“The stakes are high. Without a cohesive, coordinated approach, limited risk and control resources may not be deployed effectively, and significant risks may not be identified or managed appropriately…The problem can exist in any organization, regardless of whether a formal enterprise risk management framework is used. Although risk management frameworks can effectively identify the types of risks that modern businesses must control, these frameworks are largely silent about how specific duties should be assigned and coordinated within the organization… The Three Lines of Defense model provides a simple and effective way to enhance communications on risk management and control by clarifying essential roles and duties. It provides a fresh look at operations, helping to assure the ongoing success of risk management initiatives, and it is appropriate for any organization…” – 2013 IIA paper called The Three Lines of Defense in Effective Risk Management and Control

This model, however, had been around since at least the 1990s, and many of those in financial services and auditing firms had used it for at least that long. As an example, separately, the Committee of Sponsoring Organizations of the Treadway Commission (COSO) had developed its own risk model (pictured below) for evaluating internal controls back in 1992. Then in 2015, COSO wrote a paper on “Leveraging COSO Across the Three Lines of Defense”, helping to align COSO’s framework to the 3LOD. The COSO model is pictured below.

The model’s use continued to spread to organizations that were embracing risk management governance and internal control assurance. The figure below is from CoBIT 5 for Risk from the ISACA organization and helps further illustrate the current model and their adoption of this model.
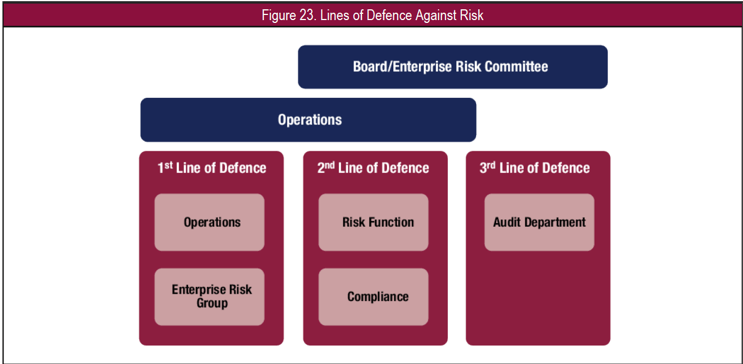
Some organizations that had embraced 3LOD years prior, had already been tweaking it to adapt more effectively within their organizations. Some also have expanded to go to four or even five lines of defense. While this adapting to fit, stretching, or blurring together can happen, the key things to keep clearly defined are the roles and responsibilities, and perhaps most importantly, the accountability definitions for each of the intended three lines. For example, in 2015, the Financial Stability Institute published their paper discussing the issues with 3LOD
( https://www.guidepointsecurity.com/wp-content/uploads/2019/11/fsipapers11.pdf ) and recommended four lines of defense for financial institutions.
Interestingly, these models were created out of a need to head off internal fraudulent activities, the ultimate “insider risk”. For example, as previously mentioned, IIA wrote their 2013 paper in the wake of the 2008 financial crisis, caused by fraudulent actions in some banks. But it doesn’t stop there. Per COSO’s site, “COSO was organized in 1985 to sponsor the National Commission on Fraudulent Financial Reporting, an independent private-sector initiative that studied the causal factors that can lead to fraudulent financial reporting. It also developed recommendations for public companies and their independent auditors, for the SEC and other regulators, and for financial institutions.” Let’s not forget that the Sarbanes-Oxley Act of 2002 (SOX) was passed to curb widespread fraudulent corporate financial reporting that created scandals in the early 2000s that included Enron, WorldCom, and Arthur Anderson. It also established the PCAOB, the watchdog for the SEC to begin overseeing the auditing firms. Up to this point, while corporations were legally responsible, CEOs were not. After that, the auditing industry adopted the COSO framework to help with evaluating SOX compliance. Then to come full circle, COSO adopted the 3LOD in 2015, as we mentioned above.
Actually, it wouldn’t be a far stretch to say that the 3LOD borrows from a basic military strategy of “defense in depth”, which is also leveraged for security architectures. (In 2010, the NSA, wrote a white paper about applying those principles to the information security assurance space.) One doesn’t have to think hard for a physical corollary – just consider the castles of old. Defense in depth may actually go back as far as “a possible early example of this…at the Battle of Cannae in 216 BC when Hannibal employed this maneuver in order to encircle and destroy eight Roman legions…Edward Luttwak used the term to describe his theory of the defensive strategy employed by the Late Roman army in the 3rd and 4th centuries AD.”[1] Several major wars since then have employed it, including the American Revolutionary War and WWI and II, just to name a few.
Why is this important for us as security professionals? All of us have an almost DNA-level foundational need to practice effective risk management in our daily professional lives. We are all impacted on some level by the regulatory directions and these frameworks and directives, and our organizations need to work within these frameworks, regulatory mandates, and many are being audited against them.
We can all watch how the proposed changes to the 3LOD unfolds (https://global.theiia.org/about/about-internal-auditing/Pages/Three-Lines-of-Defense-Review-Exposure-Document-and-Survey.aspx). It’s
also good to keep in mind that frameworks are like a set of highway guardrails
to keep us from going off the road, but still can allow us some lateral
movement to integrate and leverage to the most effective means possible for our
individual organizations, all the while addressing the issues they were
originally intended for. So, changes that lead to maturing and more effective
control assurances and risk management are always welcome.
About GuidePoint
GuidePoint Security LLC provides customized, innovative and valuable information security solutions and proven cybersecurity expertise that enable commercial and federal organizations to successfully achieve their security and business goals. By embracing new technologies, GuidePoint Security helps clients recognize the threats, understand the solutions, and mitigate the risks present in their evolving IT environments. Headquartered in Herndon, Virginia, GuidePoint Security is a small business, and classification can be found with the System for Award Management (SAM). Learn more at www.guidepointsecurity.com.
Contributing Authors
Brian Betterton, Practice Director, Governance and Risk, GuidePoint Security
Brian Betterton
Practice Director - Governance & Risk,
GuidePoint Security
Brian is the Practice Director of Governance and Risk at GuidePoint Security. His professional experience started in 2001 and includes creating strategy, leading, building and maturing security, risk, and compliance programs. He has led and participated in programs throughout the world for industries such as financial, critical infrastructure/energy, healthcare, hospitality, technology cloud services and retail verticals. He has held various roles, including technologist, consultant, architect, strategist and leader of global security programs. He has been included in the Security Executive Rankings and, in 2012, he was on the leadership team selected to SC Magazine’s European shortlist for Information Security Team of the Year.
Brian holds several certifications, including Certified Information Systems Security Professional (CISSP) and Certified Information Security Manager (CISM).