vSOC SPOT Report: Cisco Adaptive Security Appliance RCE & Denial of Service Vulnerability
Posted by: GuidePoint Security
Update (2018-01-31): SNORT Signatures
After further research, vSOC has located Snort signatures published by the fox-srt team, which can detect exploitation of this vulnerability.
# IDS signatures for https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180129-asa1: alert udp any any -> any 500 (msg:"FOX-SRT - Suspicious - Possible Fragmented Cisco IKE/isakmp Packet HeapSpray (CVE-2018-0101)"; flow:to_server; content:"|84|"; offset:16; depth:1; content:"|02 08 |"; distance:1; within:2; fast_pattern; byte_test:4,>,5000,4,relative; byte_test:2,>,5000,10,relative; byte_extract:4,36,fragment_match; byte_test:4,=,fragment_match,52,relative; byte_test:4,=,fragment_match,136,relative; byte_test:4,=,fragment_match,236,relative; threshold:type limit, track by_dst, count 1, seconds 600; classtype:attempted-admin; sid:21002339; rev:4;) alert udp any any -> any 500 (msg:"FOX-SRT - Exploit - Possible Shellcode in Cisco IKE/isakmp - tcp/CONNECT/"; content:"tcp/CONNECT/"; fast_pattern:only; threshold:type limit, track by_src, count 1, seconds 600; priority:1; classtype:attempted-admin; sid:21002340; rev:2;)
These alerts have been provided by fox-srt and can be found at their GitHub site: https://gist.github.com/fox-srt/09401dfdfc15652b22956b9cc59f71cb
Overview
On Monday January 29th, Cisco released a statement to customers that they had identified a vulnerability (CVE-2018-0101) affecting Cisco ASA (Adaptive Security Appliance) and Cisco Firepower Threat Defense Appliances via the Secure Sockets Layer (SSL) VPN functionality of the devices which could allow an unauthenticated remote attacker to create a denial of service condition by reloading the device to remotely execute specially crafted malicious code. The vulnerability is due to an attempt to double free a region of memory when the webvpn feature is turned on for the Cisco ASA device.
Attack Details
The vulnerability makes this very easy to exploit and as a result, it was rated a 10 out of 10 on the CVSS (Common Vulnerability Scoring System). The attack involves an attacker sending multiple crafted malformed XML packets to the Cisco ASA devices and Cisco Firepower software. If the exploit is successful, the attacker will then have the ability to execute unauthorized code on the devices. Depending on the nature of the code, the attacker can gain full control over the device. This attack does not require physical access and can be carried out remotely. The ASA device(s) are only vulnerable if they have the webvpn feature enabled within the OS settings.
Attack Detection and Prevention
Attack patterns will vary once exploits are developed and used in the wild. Some possible detection methods include monitoring XML packets sent to Cisco ASA hosts via packet capture, or to monitor for sudden regular spikes in traffic sent to Cisco ASA hosts, as these spikes would likely be an attempt to force constant restarts on the device. To determine whether the webvpn service is enabled, administrators can use the command show running-config webvpn at the command line. Additionally, the show version command can be run to verify which version of Cisco ASA Software is running on the device. The Cisco Adaptive Security Device Manager (ASDM) can also show the software release in the table that appears by the login window, or in the upper-left corner of the ASDM interface.
The show version command will also show the release version for Cisco Firepower Threat Defense (FTD) devices. Version 6.2.2 of FTD devices are vulnerable because it incorporates code from both Firepower and ASA devices, as it was the first release that supported the Remote Access VPN feature.
Affected Systems
- 3000 Series Industrial Security Appliance (ISA)
- ASA 5500 Series Adaptive Security Appliances
- ASA 5500-X Series Next-Generation Firewalls
- ASA Services Module for Cisco Catalyst 6500 Series Switches and Cisco 7600 Series Routers
- ASA 1000V Cloud Firewall
- Adaptive Security Virtual Appliance (ASAv)
- Firepower 2100 Series Security Appliance
- Firepower 4110 Security Appliance
- Firepower 9300 ASA Security Module
- Firepower Threat Defense Software
Recommendations
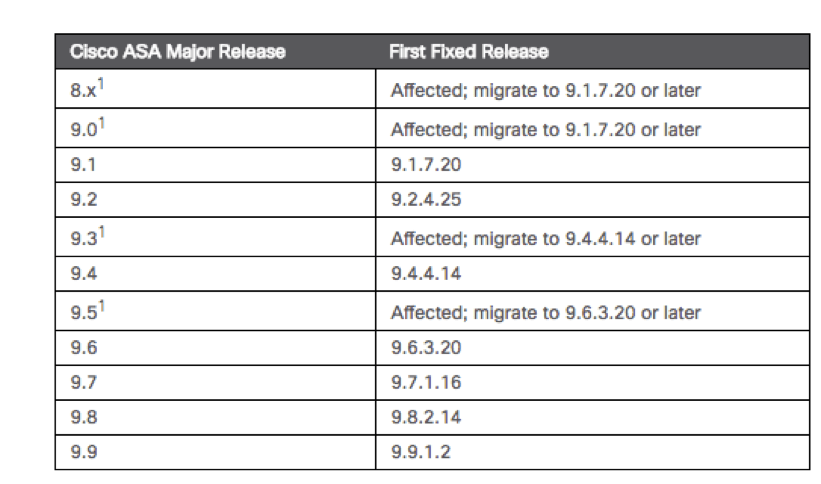
Cisco has released several tables showing the versions to update to and the original ASA major release. It is recommended to ensure both the ASA devices and FTD software is updated to the version released to counteract the vulnerability.
[1] Cisco ASA Major release table (Cisco, 2018)

Workarounds
There are no workarounds for this vulnerability. However, Cisco has already released updates that address this vulnerability. Versions that include this fix are listed in the ASA Major release table above.
Additional Resouces
- https://nvd.nist.gov/vuln/detail/CVE-2018-0101
- [1] https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180129-asa1
GuidePoint Security