
Incident Response & Threat Intelligence
In Order to Identify and Respond to Incidents as Early as Possible, You Need an Effective Threat Intelligence Program and a Robust Incident Response Framework
INCIDENT RESPONSE & THREAT INTELLIGENCE CHALLENGES
How are You Preparing for, Responding to and Efficiently Resolving Cybersecurity Incidents?
Cyber attacks happen on a regular basis – across all industries and organizations of all sizes. Your preparedness and ability to quickly respond to threats and recover requires the right personnel, processes and solutions.

277 days
is the average time it takes to identify and contain a data breach
Ponemon Institute 2023 Cost of a Data Breach
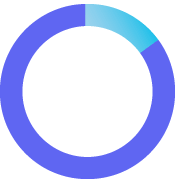
54 days
faster to resolve a breach if there’s an IR team and IR plan testing in place
Ponemon Institute 2023 Cost of a Data Breach

$1.49m
less in costs for organizations with IR programs compared to those without
Ponemon Institute 2023 Cost of a Data Breach
INCIDENT RESPONSE & THREAT INTELLIGENCE PRACTICE
Proactive and Reactive Incident Response & Threat Intelligence Services
Our Incident Response & Threat Intelligence practice provides proactive and reactive services to help organizations prepare for, respond to and recover from a security incident.
Whether it’s Ransomware, Insider Threats or Data Breaches, our team helps customers quickly respond to these incidents so they can get back to business.
Our Threat Intelligence capabilities help our customers understand the threat actors and the TTPs they leverage to target their environment and operationalize this intel to implement the right countermeasures.
Our Application Security Commitment to You
We will help you raise the AppSec bar by:
- Focusing testing efforts in order to maximize the coverage of an application and ensure that the most security sensitive functions and features are assessed.
- Providing you with actionable insights into how an adversary can currently leverage or exploit real issues or vulnerabilities in your business-critical applications—allowing you to not only reduce risk but also the cost of remediation.
- Assessing the gaps in your current development lifecycle and provide implementation recommendations meant to strengthen overall efforts and reduce risk.
- Moving the needle with your Application Security program—whether it’s a gap analysis, program development, AppSec artifact creation (secure coding checklists, standards, etc.), onboarding, socialization or a unique need that doesn’t fit into a fixed offering.
INCIDENT RESPONSE & THREAT INTELLIGENCE SERVICES
Prepare for, Respond to & Resolve Security Incidents Through an Effective Threat Intelligence Program & IR Framework
Explore our Incident Response & Threat Intelligence services:
Whether you need a dedicated Incident Response (IR) or Threat Intelligence (TI) team or an evaluation of your current programs, our expert practitioners are ready to assess your program maturity, provide critical intel to improve your defenses, develop and test your plans, respond to and help you recover from an incident.

Threat Actor
Communications
Retainer
Be ready to negotiate the best possible outcome if victimized by ransomware.

IR Enablement
Services
Ensure your team is equipped with required capabilities to effectively respond to threats.

Incident Response Services
Quickly investigate & understand the full scope of an incident.

Ransomware Response Services
Navigate ransomware variants, threat actors & techniques to ensure an effective outcome.

Digital Forensics Services
Preserve, collect & analyze electronic data to support investigations & litigation.

Tabletop Exercises
Run relevant incident scenario simulations to identify potential gaps in your IR process.

Purple Team
Assessments
Validate, extend & expand your IR capabilities, while actively working to reduce your threat profile.

IR Playbook &
Runbook
Development
Ensure you’re following a predefined process during a response effort.

IR Plan Development
& Review
Be prepared with a well-defined process for responding to an incident.

Threat Intelligence as a Service
Fully managed threat intelligence program from conception to execution.
INCIDENT RESPONSE & THREAT INTELLIGENCE OUTCOMES
Ensure Best Practices for When a Security Incident Happens
Our dedicated IR practitioners & Threat Intelligence analysts are experienced with a wide variety of industry standard tools and solutions that provide the required visibility across your network, endpoints and other systems to perform efficient and comprehensive investigation of an incident.
Ensure Incident Preparedness
Hunt for threats, gain critical threat intelligence & ensure you have an experienced team on standby
Quickly Respond & Recover
Investigate & understand the full scope of an incident, preserve necessary data and ensure an effective outcome
Develop & Test Your Incident Response Plans
Identify gaps in your IR process, establish & enforce predefined a response process, validate & extend your capabilities
Gain a Fully Managed TI Program
From conception to execution, gain an entire Threat Intelligence program that meets your organization’s needs
Why GuidePoint Security
Your Elite, Highly-trained Team
More than 50% of our workforce consists of tenured cybersecurity engineers, architects and consultants. We are also highly certified across industry standards as well as hundreds of cybersecurity solutions.
Highly Trained, Highly Certified
Examples Include:








GIAC Certifications


Offensive Security Certifications
Your Trusted Advisor
Our team works side-by-side with you as your cybersecurity partner.
“GuidePoint Security is basically family. They’re always there when I need them. At the end of the day GuidePoint is always there to help and that’s how they add value.”
Mark Gilman
Security Manager




